Today was day 2 of the Microsoft Ignite in Orlando. Today I was in the focus in sessions about modern management on the move. That means, for example, Microsoft Intune, but especially the newly announced function of the “Microsoft Endpoint Manager”.
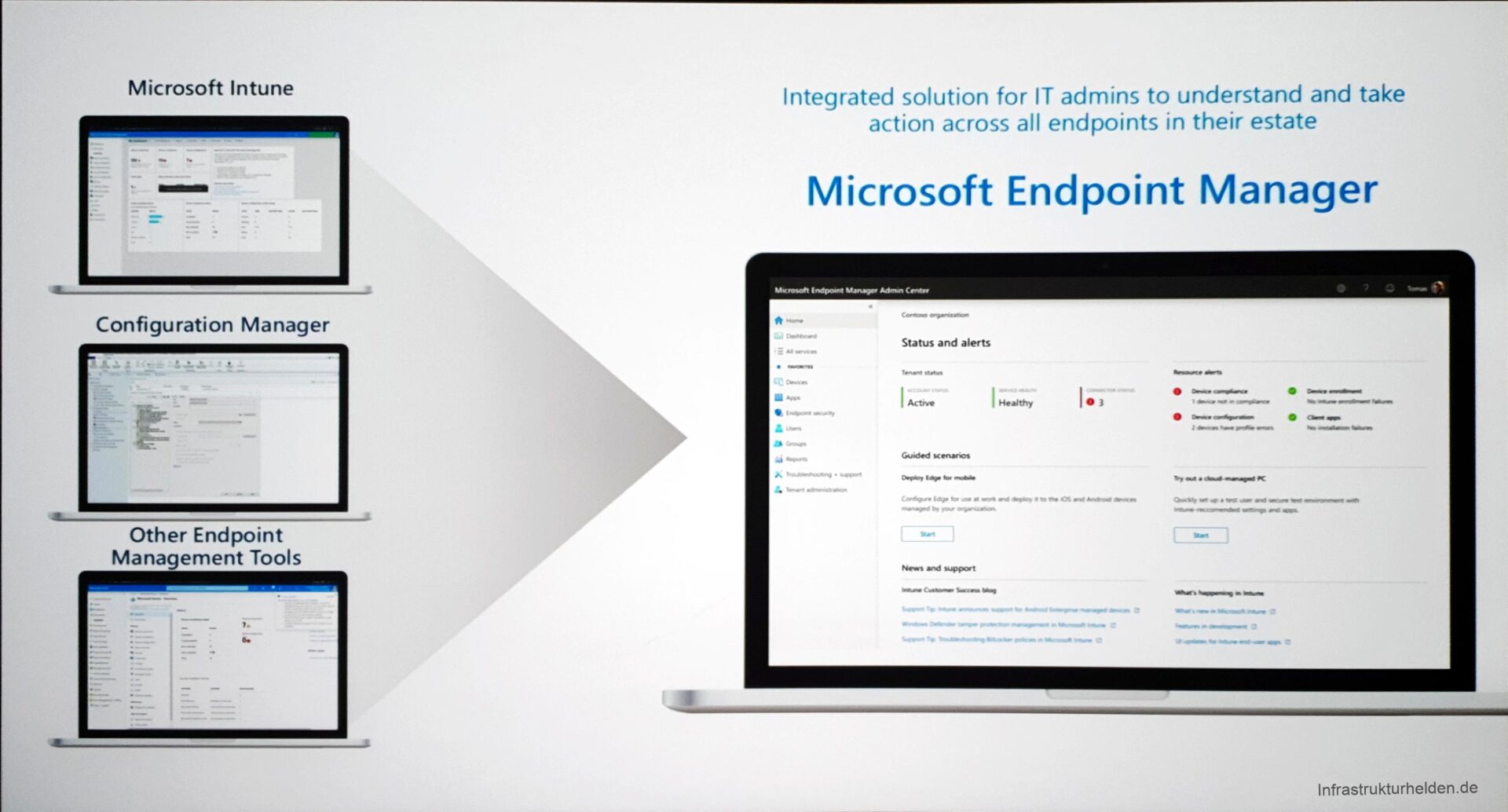
Microsoft Endpoint Manager
With the Microsoft Endpoint Manager, Microsoft wants to unite all endpoint management systems. For example, the administration of SCCM and Intune in co-management should be simplified. Through the Cloud-based Endpoint Manager, you can also administrate pure SCCM managed devices. This is made possible by some new functions in the co-management of SCCM and Intune.
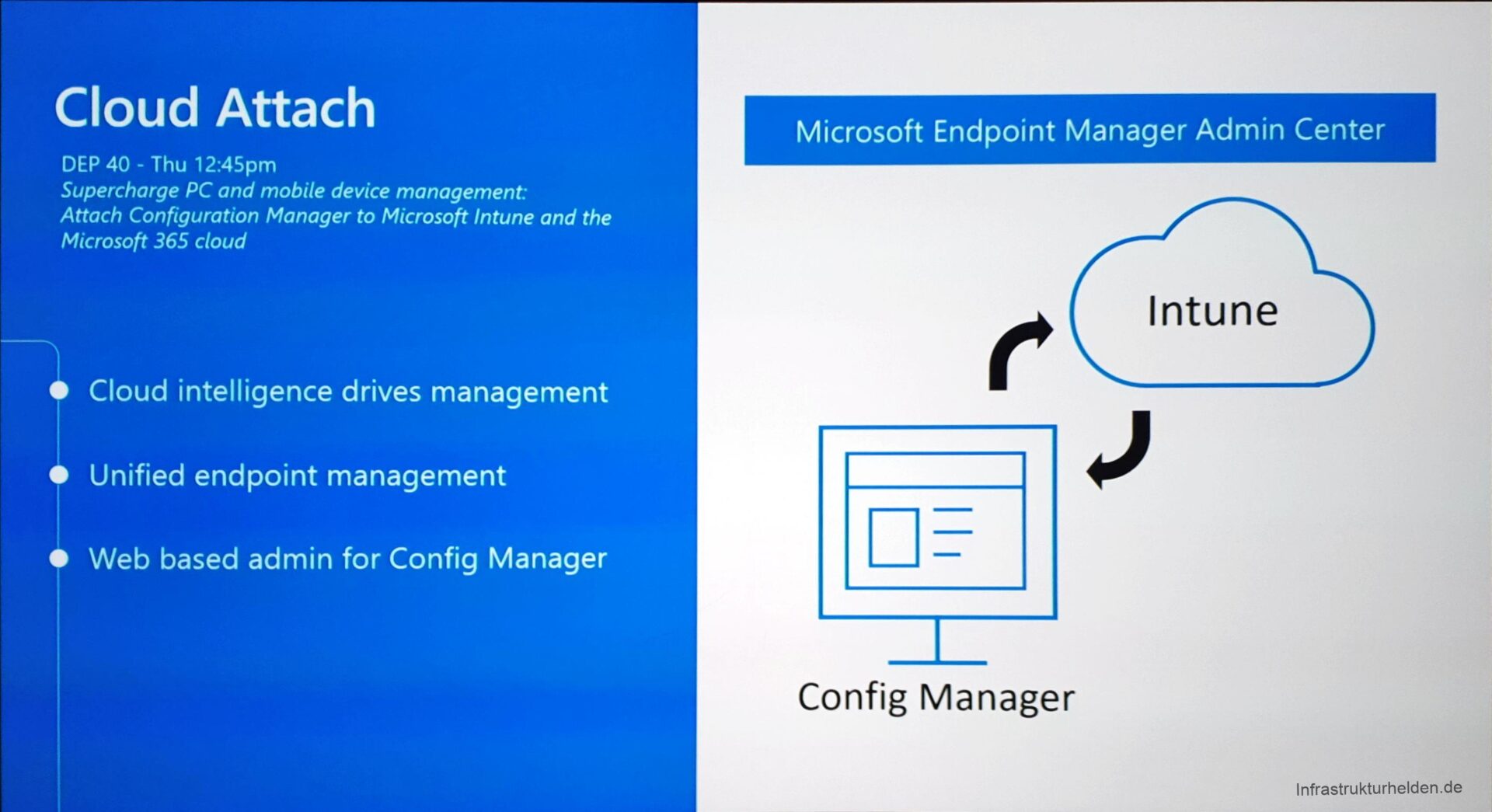
A benefit of the Endpoint Manager is that it supports role-based administration (RBAC). The Helpdesk with a suitable authorization role can also use this interface and only sees the information made available to it. This makes the permissions management much easier compared to set the SCCM permissions, the Intune permissions, the AzureAD permissions and others. It also provides a consolidated, web-based console. This implies no more admin software or administrative password hashes or tokens on the system. RBAC can also be used to hide certain security settings that may be managed by a dedicated security team.
Endpoint Manager and Licensing
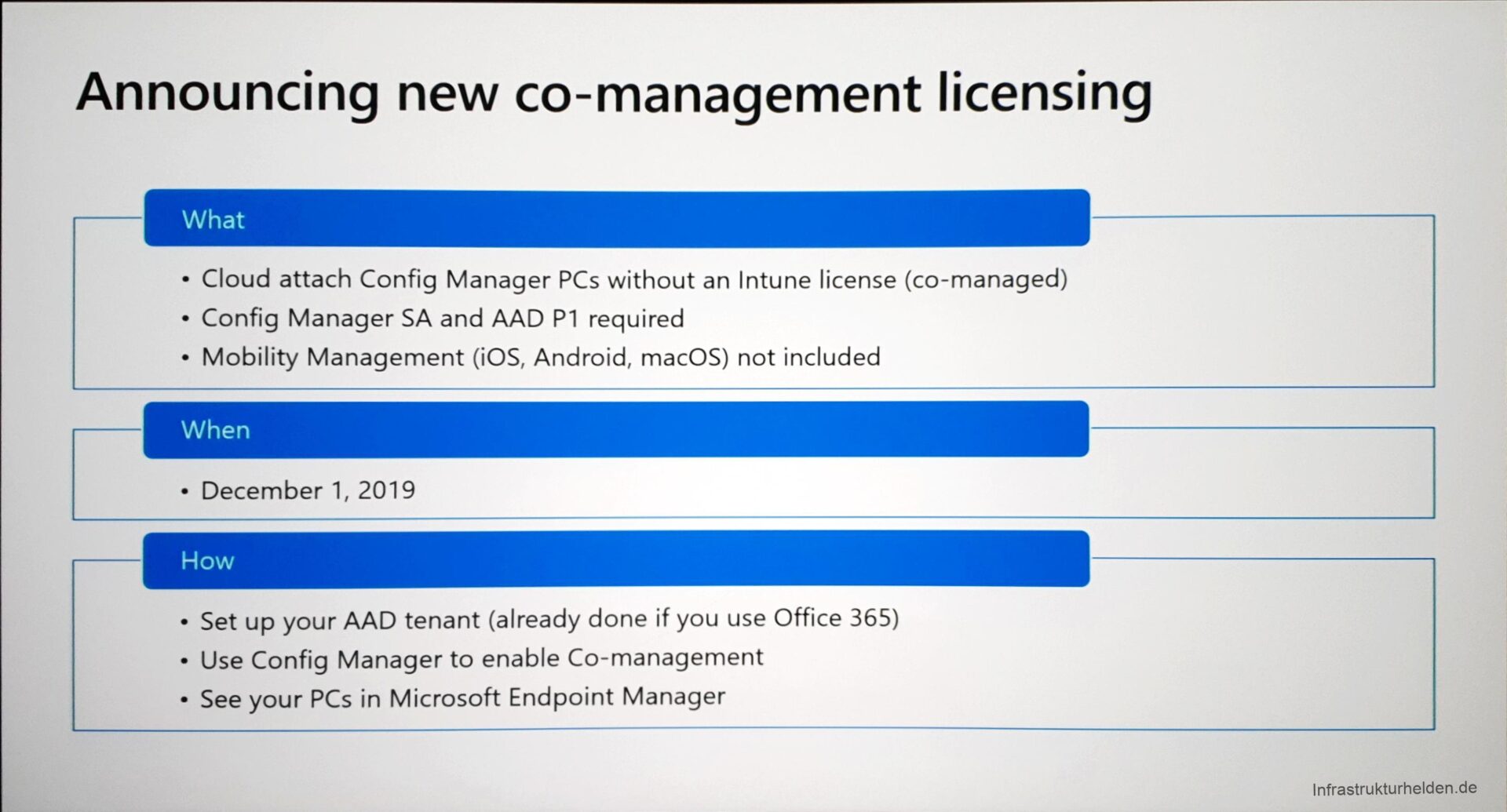
To provide a better motivation to customers, Intune licensing for SCCM customers with Software Assurance will also be facilitated. For these customers, Intune will soon be free of charge. Only an Azure AD P1 plan is needed in order to provide Intune as MDM for the systems and to extend the Azure AD with further necessary functions.
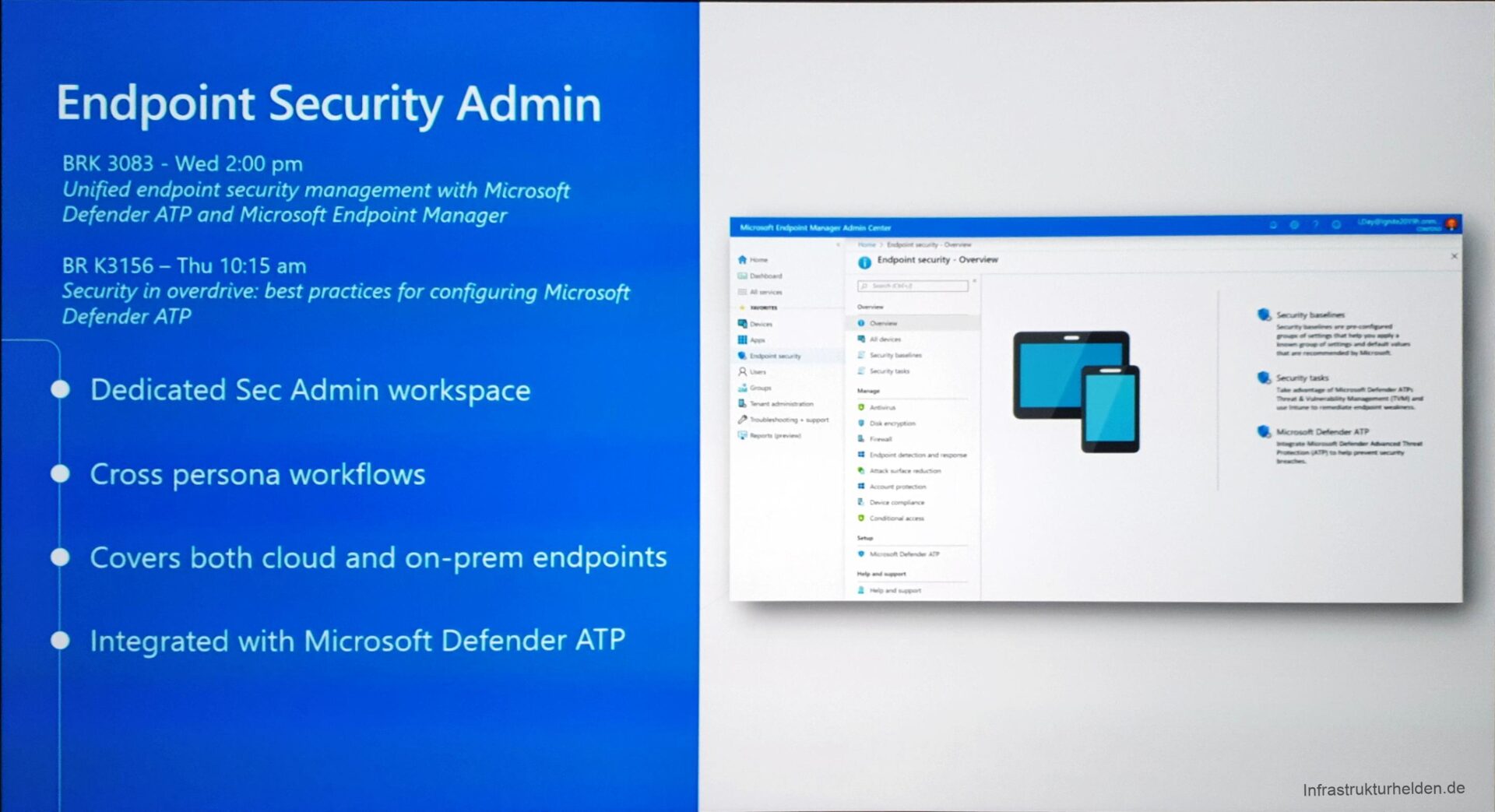
Security Admin
The Security Admin also has an extension in the pipeline. Security baselines have been around since last year, but they are now being extended. Also, security guidelines for Edge and Office 365 Pro Plus are announced.
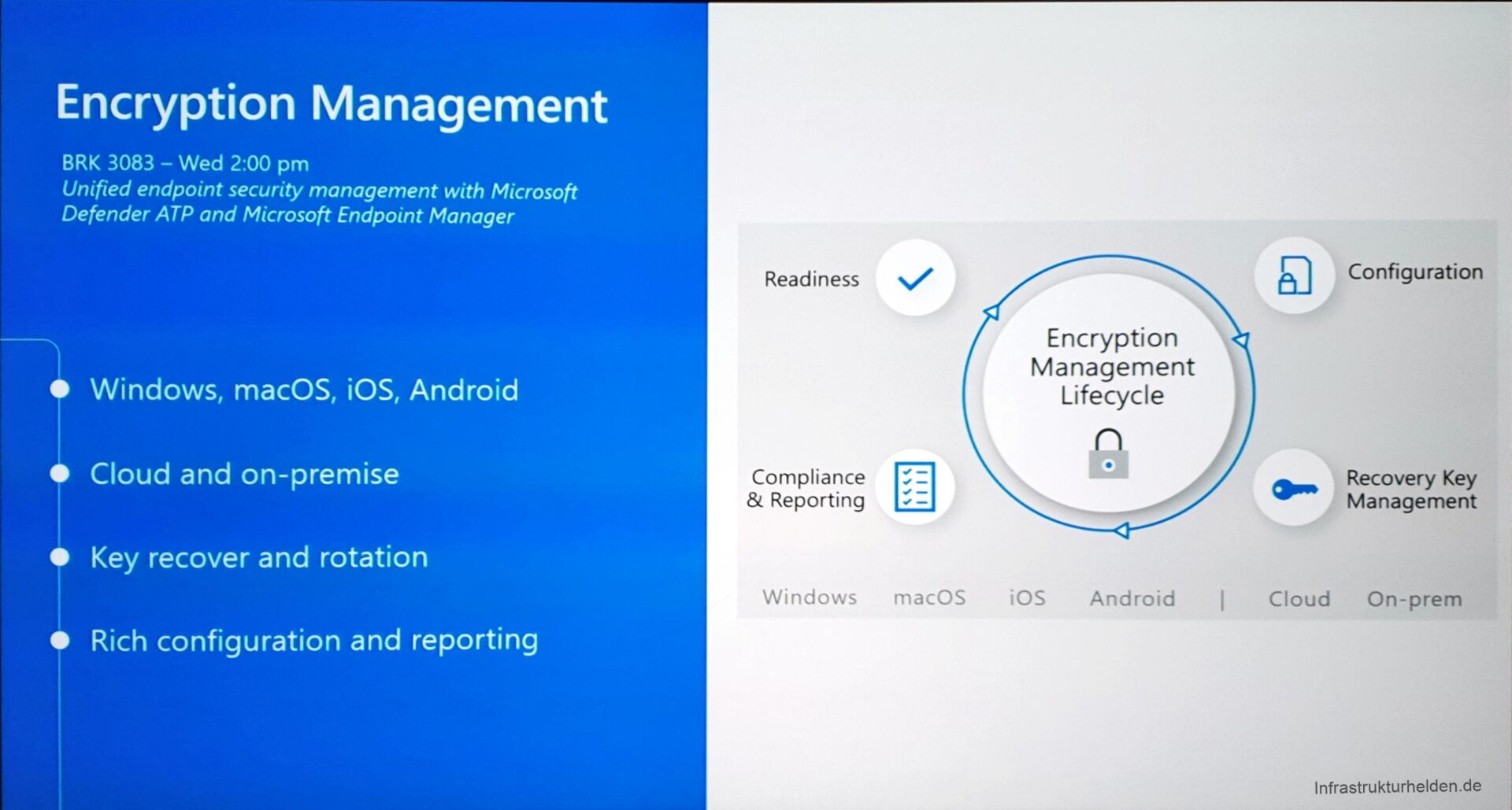
Also new are the rules for device encryption, at least for some operating systems. macOS is now also supported, including the management of the recovery key.
A lot has happened with Windows 10 as well. MBAM is already discontinued for the future. Now Intune finally gets the necessary controls to make it easy. Including saving the recovery key and recreating a recovery key via Intune. This is handy once it has been released to the customer.
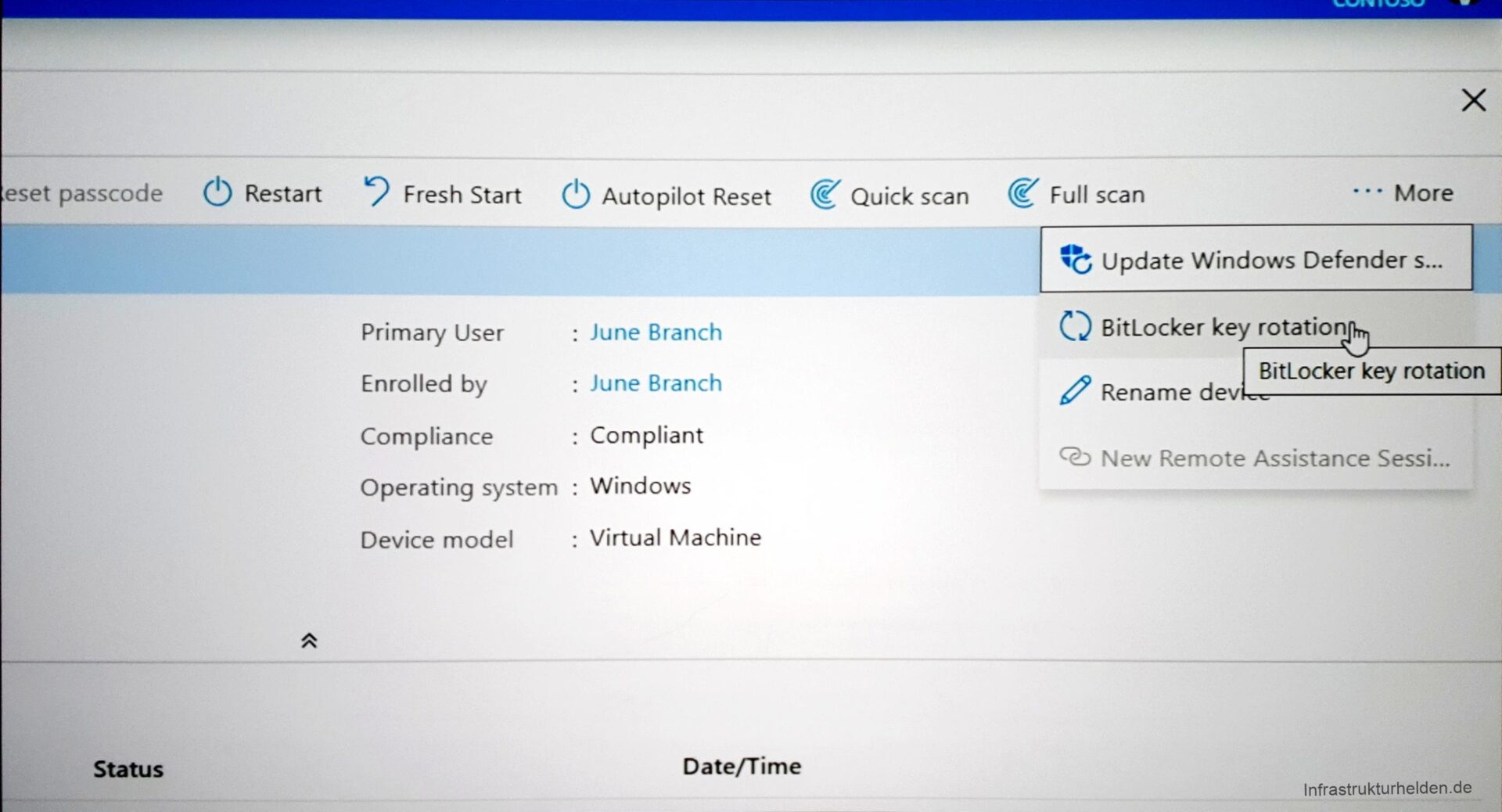
This function can be found in the Troubleshoot menu item in the Security Console.
Experience Score
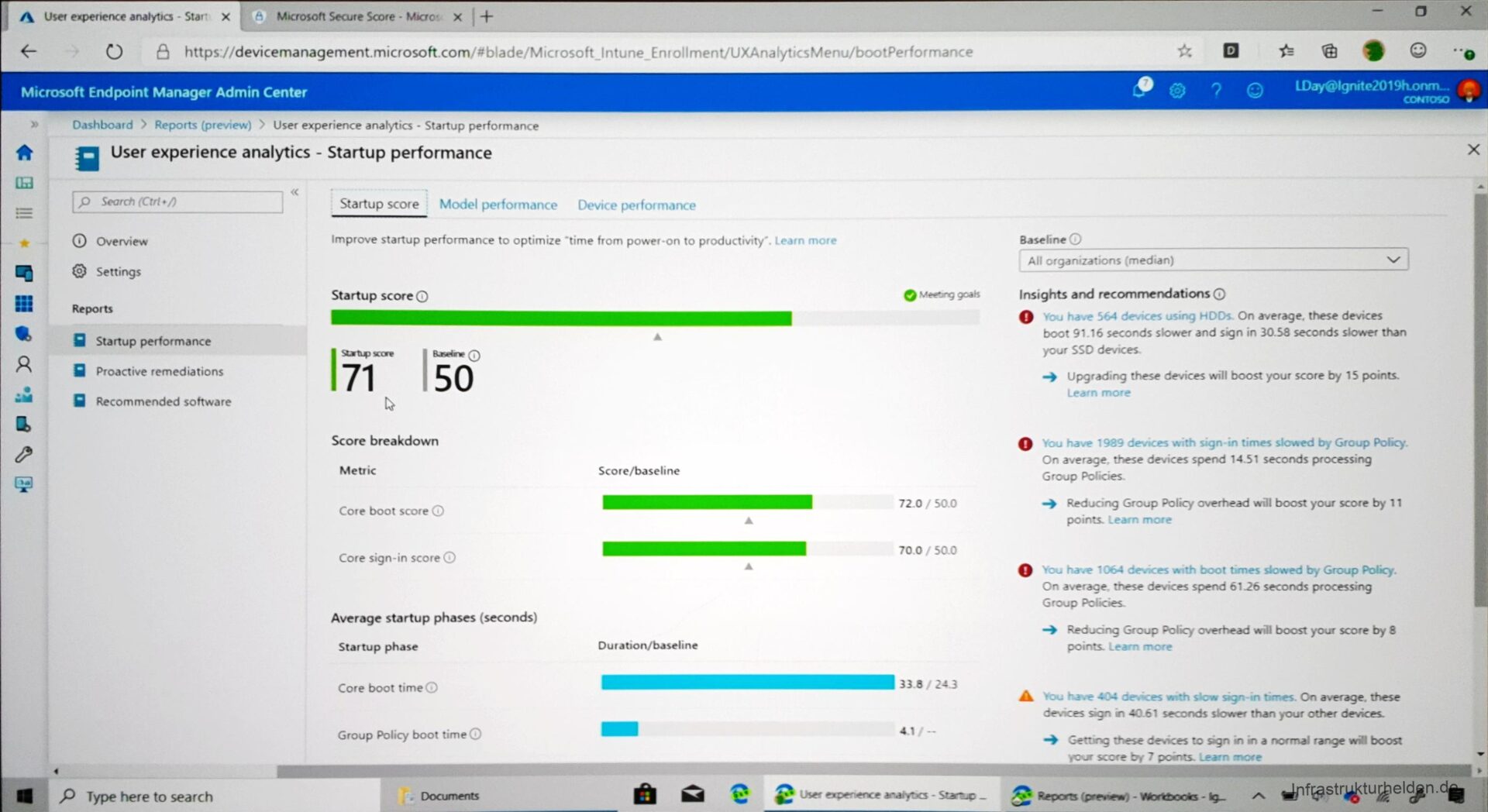
This new feature should help the IT department to find optimizations on the devices for better usability. Telemetry data and other signals of the devices will be analyzed. Possible recommendations are SSD instead of HDD or changes to the configuration. It is also interesting that these data can be sorted according to many criteria. Model-based analyses can also be performed, such as which hardware model has the longest boot time.
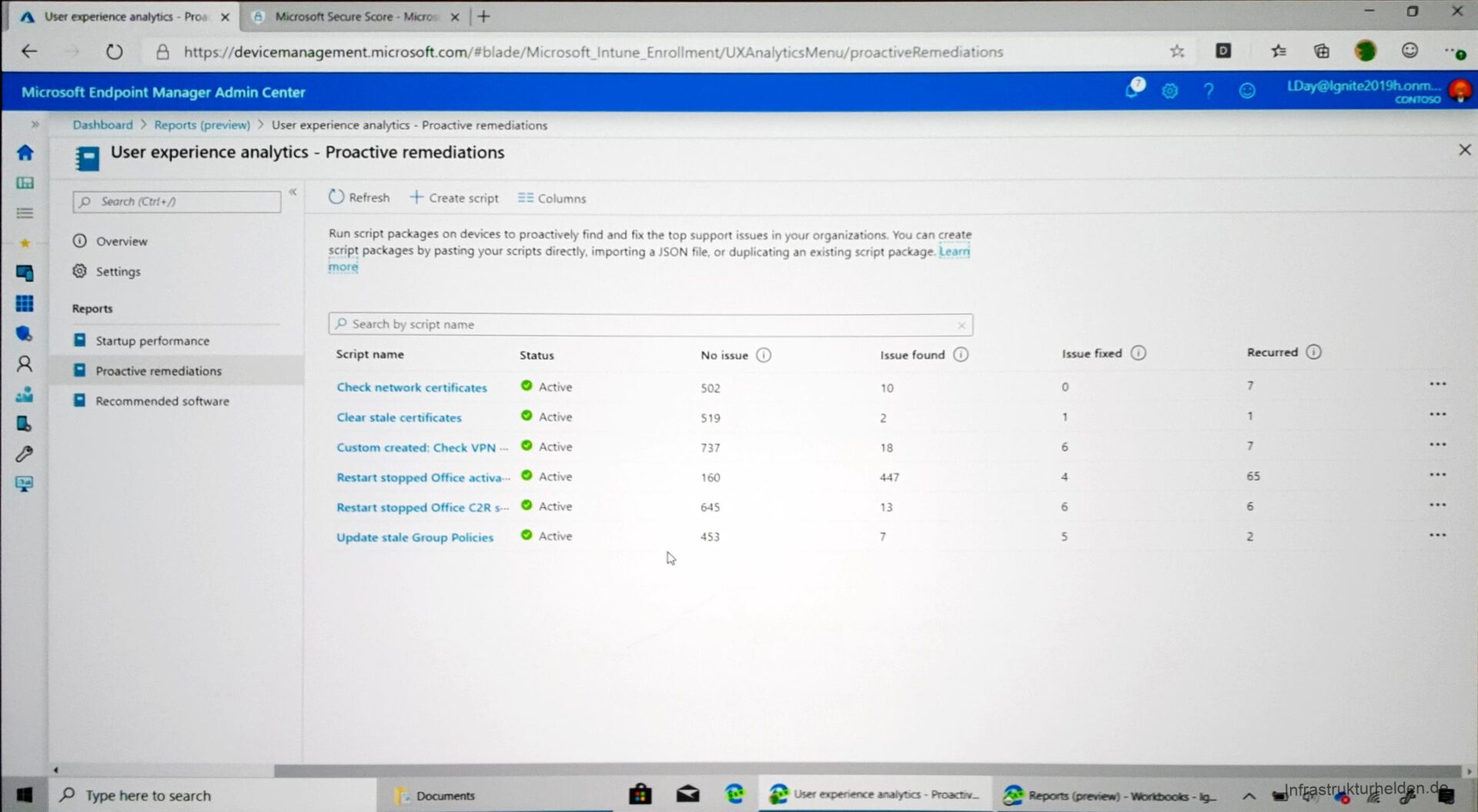
There are also scripts that are executed automatically to improve performance. The preview currently contains 6 scripts:
- Check Network Certificates
- Clear stale certificates
- Check VPN
- Restart stopped Office activation
- Restart stopped Office Click-2-Run Services
- Update stale Groupe Policy
Non-Windows Management
There are separate break-out sessions for non-Windows 10 devices.
macOS Management
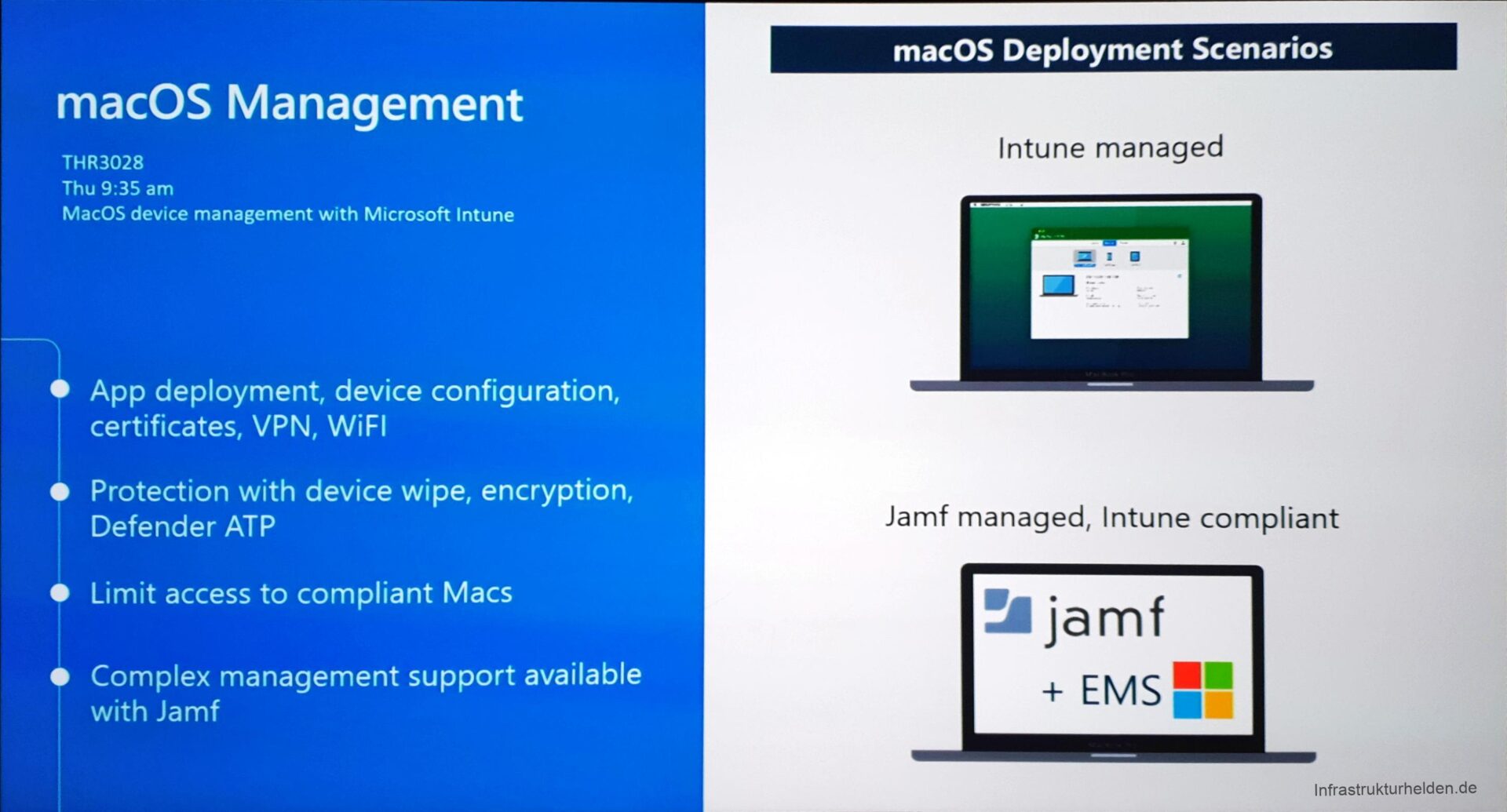
A special feature, which I would like to mention here and which was shown briefly, Intune Management for macOS devices. Until now, this was only possible through the integration of the third-party solution JAMf. At the beginning of next year, a beta for the Native solution will be released. Microsoft also said that Native will contain only one basic configuration and that JAMf will continue to be the right solution for more complex scenarios.
Another session on the subject of non-Windows devices is:
Android OS Management
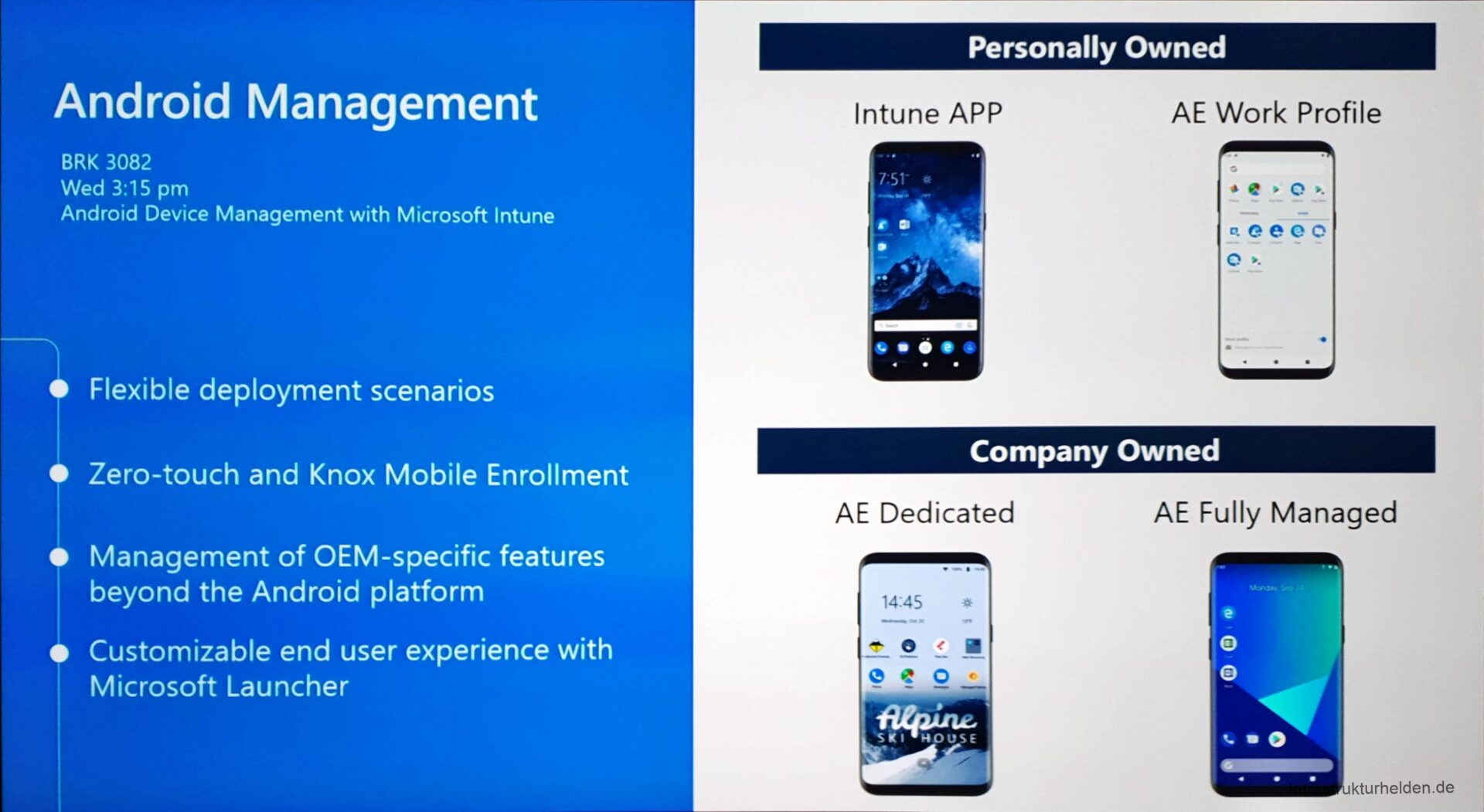
Mobile Application Management can now also be used to block the execution of corporate applications, or applications in the corporate context when a device is not secure. An example is the use of Lookout for companies to detect unauthorized or dangerous applications.
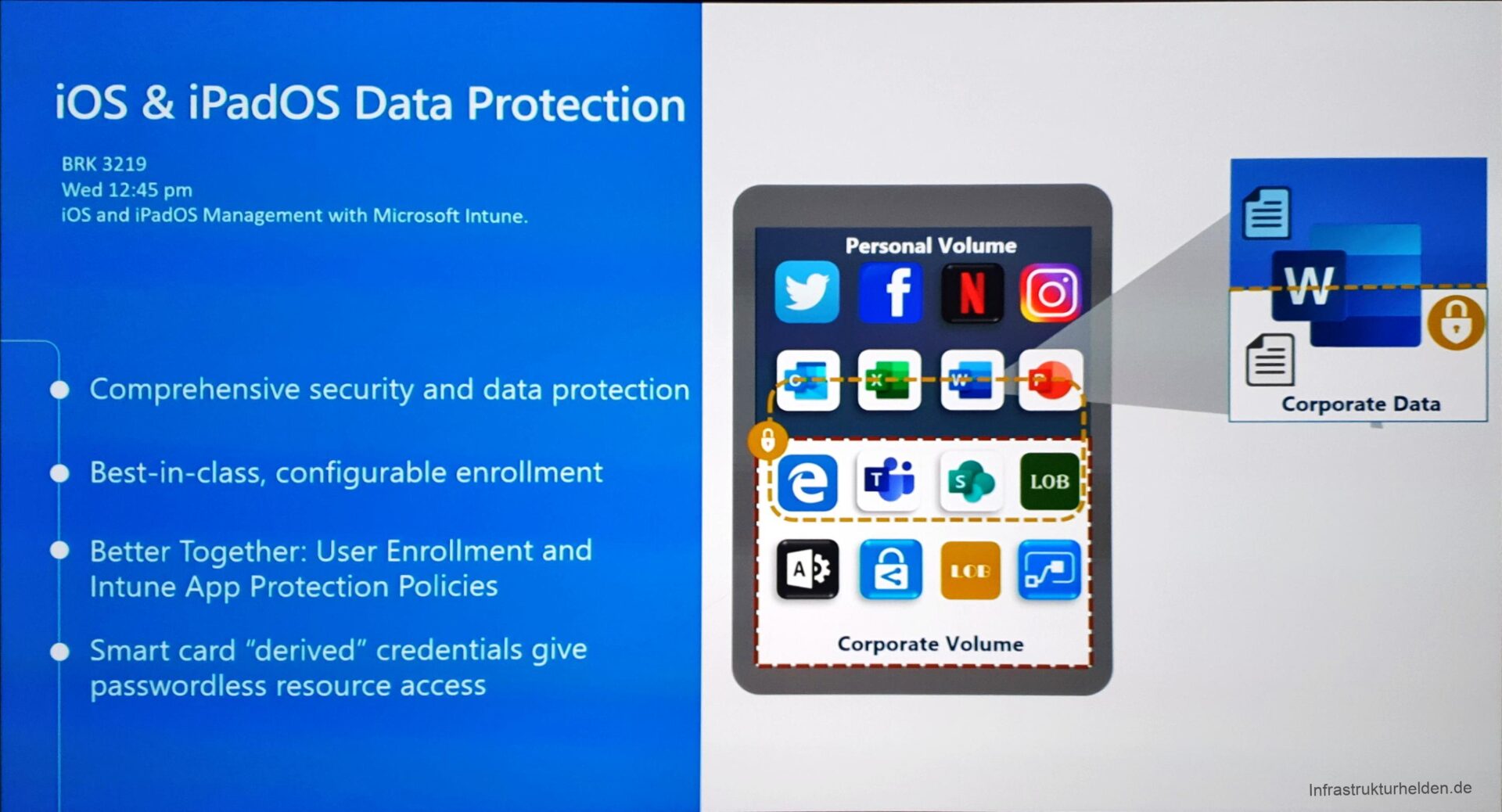
iPhone / iPad Management
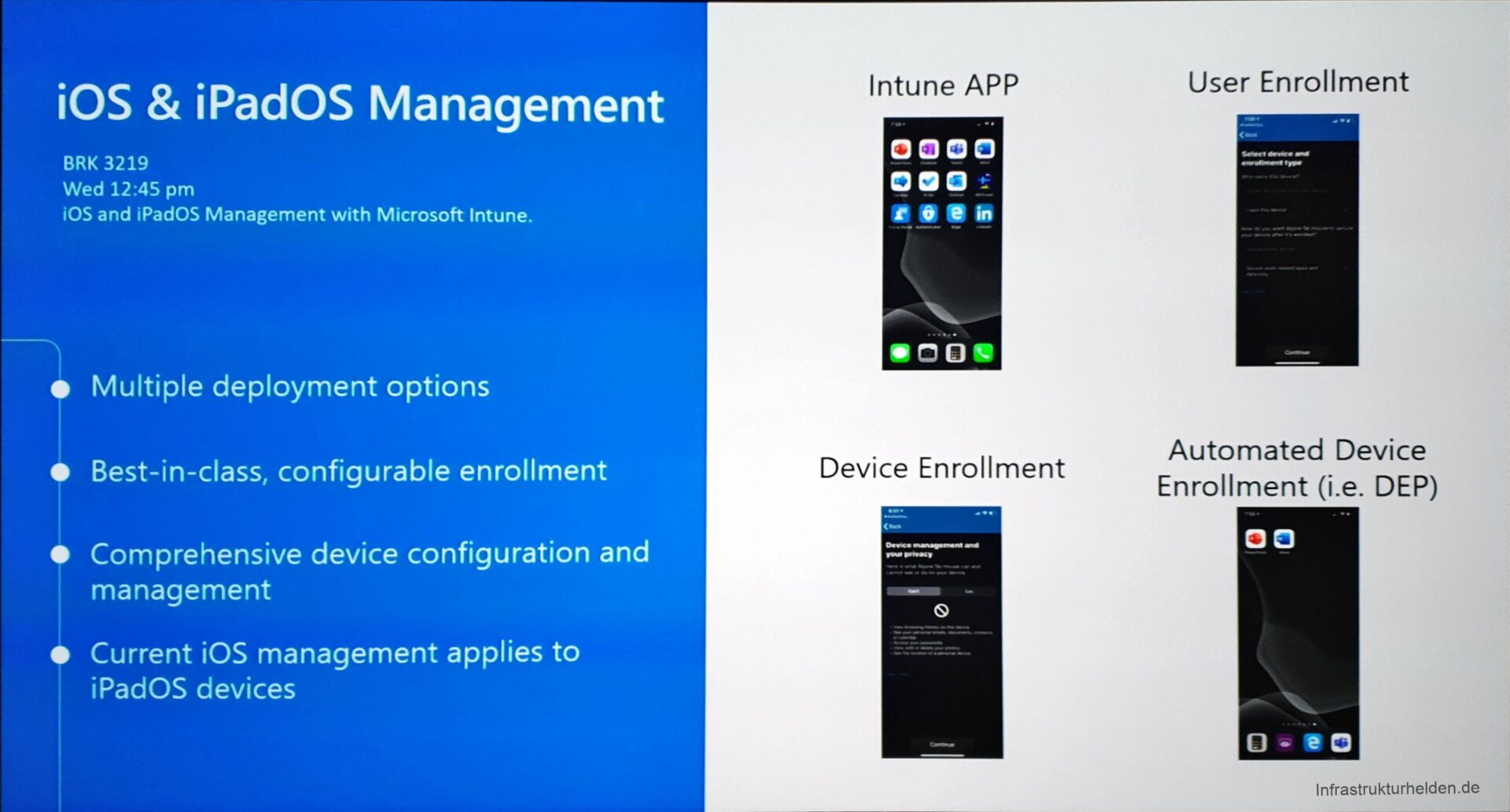
Mobile Application Management is now also supported by iPads and iPhones. A new feature is that the customers are guided by an assistant during setup. This also establishes a federation between the Apple ID and Azure AD for this user. This allows for some SSO functions.
Office Pro Plus Management
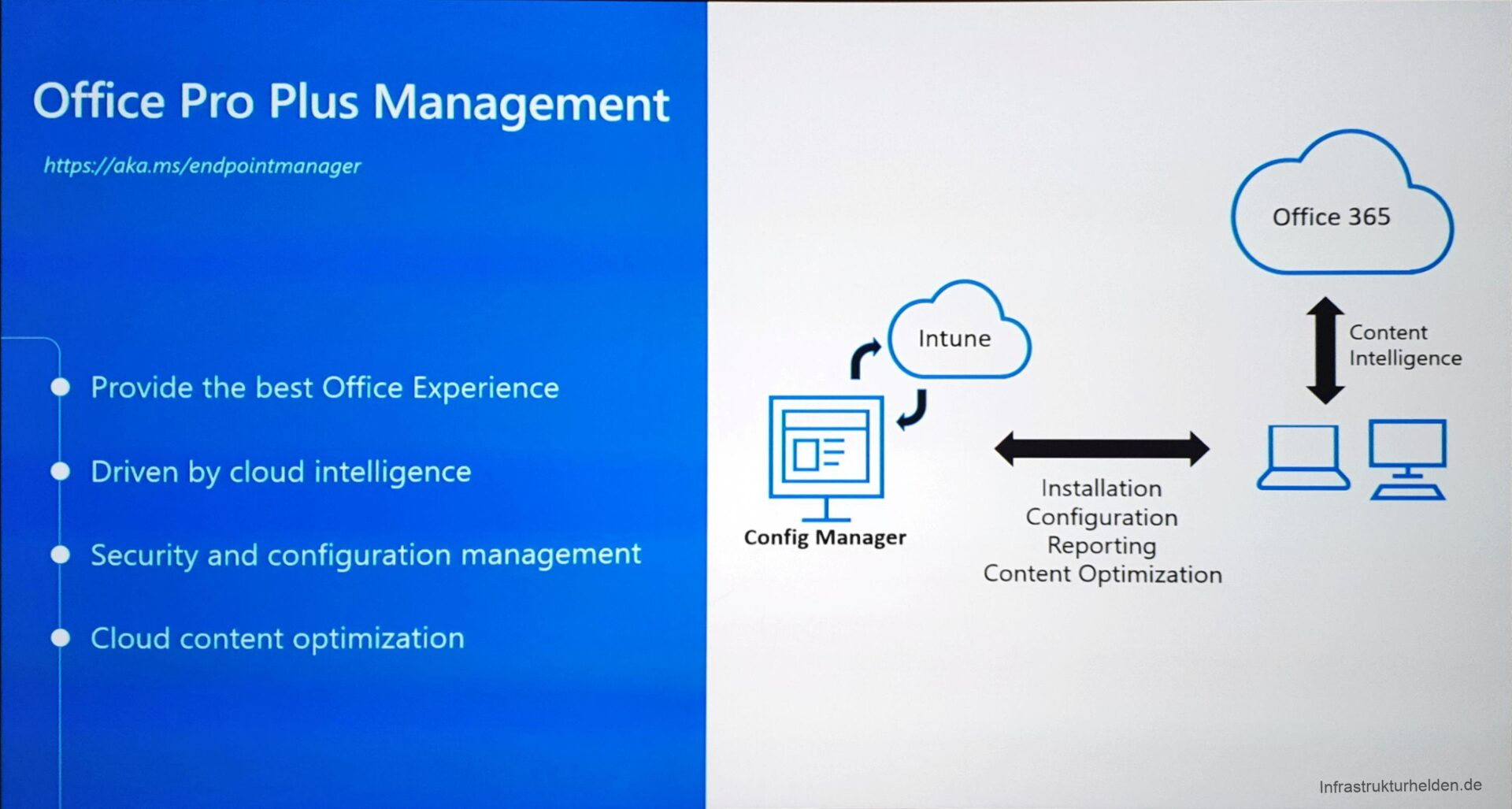
In the software assignment for Office Pro Plus, the individual programs can now also be selected for installation. The update rings can also be defined here, and other settings that were previously only possible via a config.xml can be made.
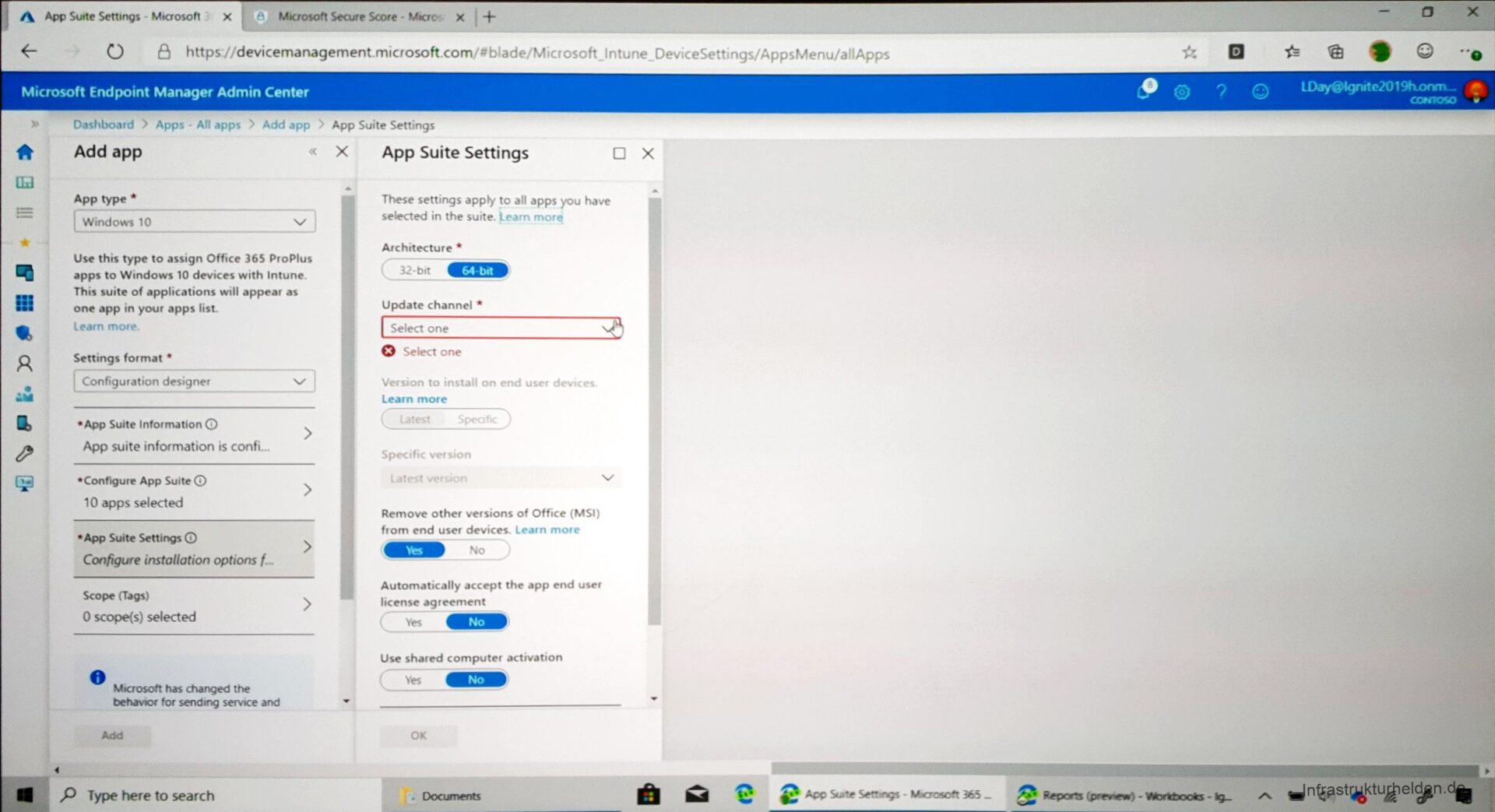
To get an exact overview of the 2169 possibilities of the administrative templates for Office, I recommend a look at the article “Administrative templates in Intune – incl. list“.
Microsoft Edge
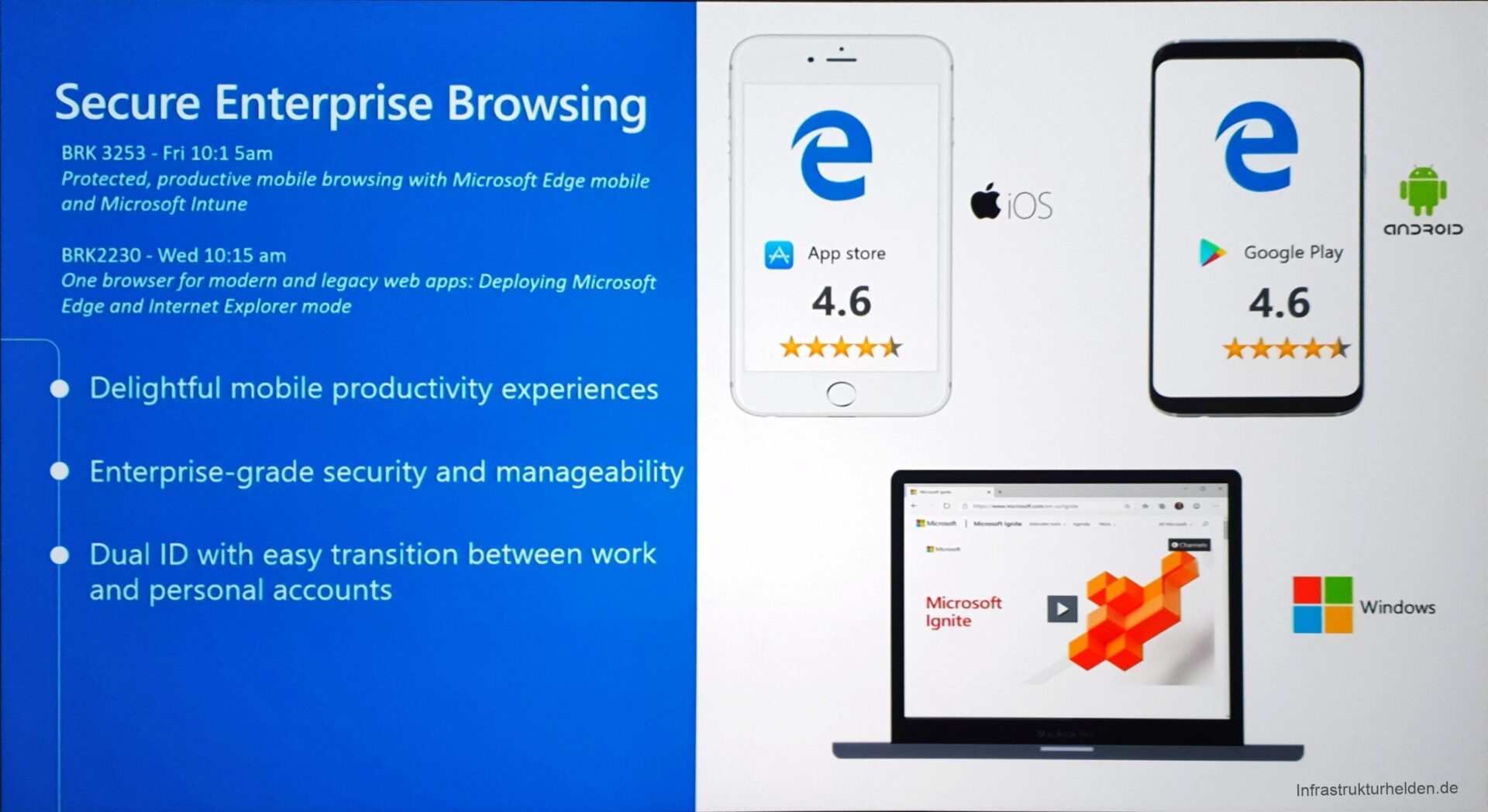
Microsoft Edge is now available for Windows 10, iOS, Android and macOS, on some of these systems still in beta. As previously described in the article “News from Edge Chromium”, it is now based on the Chromium Engine. Now it can easily be distributed to the different device types via Intune. It is possible to select the channels of the Edge Browser, for example, Beta or Release. Depending on the OS you can also make further settings. For Windows 10, the Edge can currently be controlled via 472 administrative templates. The list can be found again in the article “Administrative templates in Intune – incl. list“.
A new feature is the possibility to define business URLs in the Edge by the IT department. These are opened in the work profile and are subject to the MAM rules. All other pages are opened in the Personal Profile.
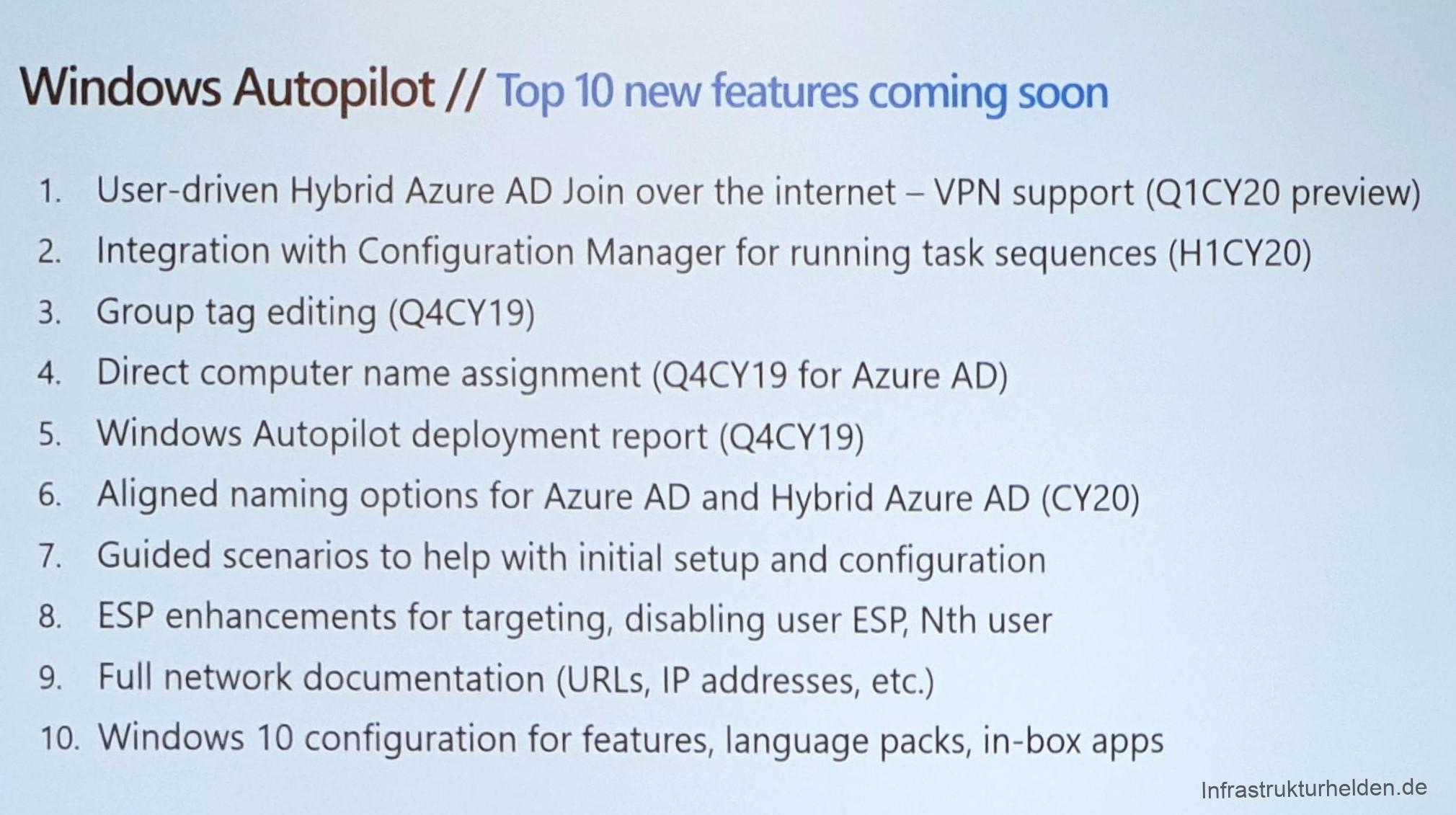
New in Autopilot
In the first sessions, only functions that were already known were reported:
- WhiteGlove (GA 2020)
- AzureAD Hybrit Join
- Administrative Vorlagen
This has changed, as expected in the session of Michael Niehaus. And here were some important and in my opinion long overdue announcements made.
Also practical is the listing of the costs for autopilot at the various OEMs. Even though I already knew them for Dell.
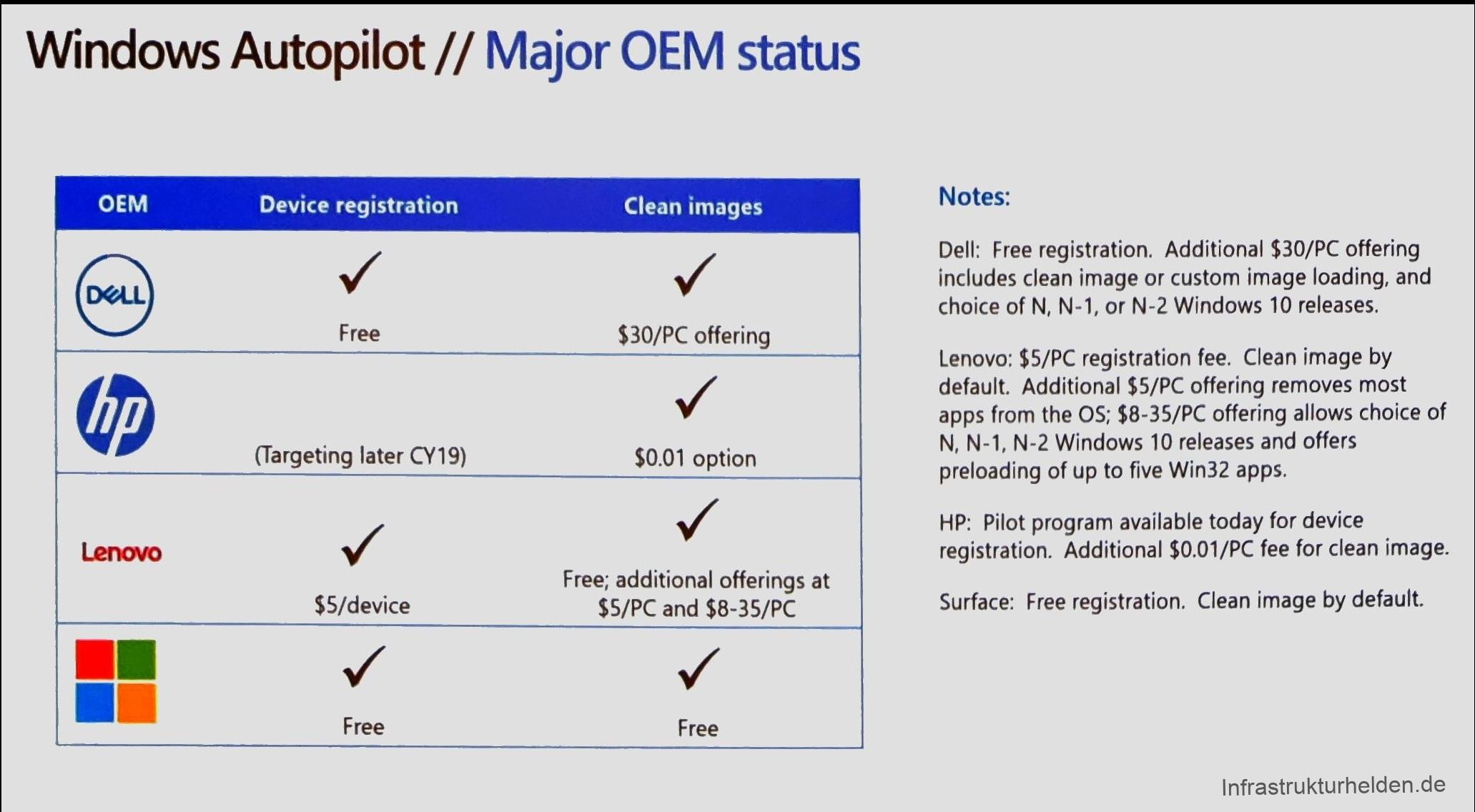
Reseller support
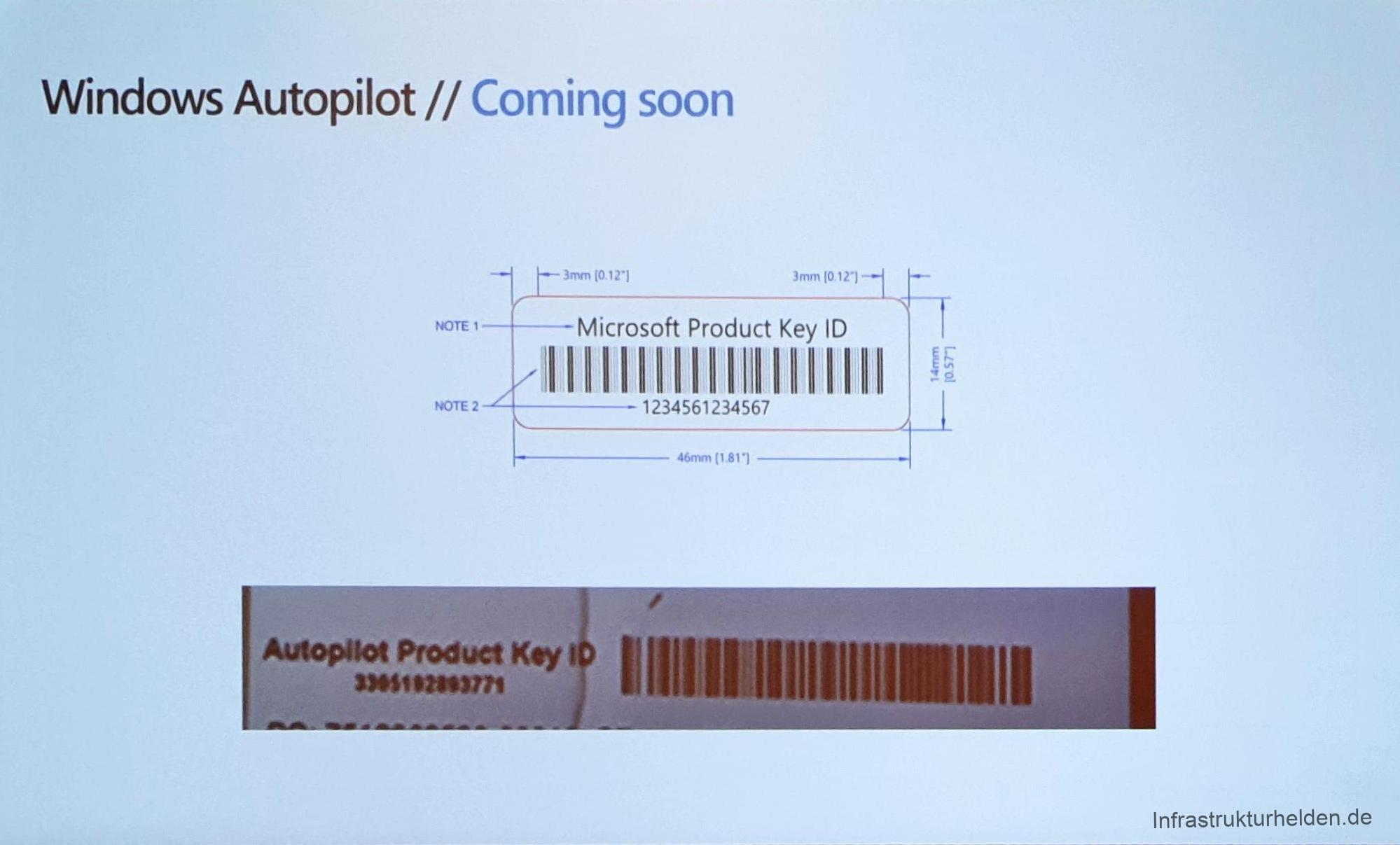
One of the innovations that are interesting for many resellers is that Microsoft has created a possibility for manufacturers to apply a product ID for Autopilot to the packaging. With this product ID, resellers can add the computer to the customer’s Azure Device Directory. How exactly this works and when Microsoft will provide the interfaces for manufacturers to generate the ID and resellers to add it to the customer Azure AD, is not clear yet.
Network optimization
Another essential change is that in future the SCCM distribution point can also serve as a cache for Intune, Office, Windows Updates 4 Business and Microsoft Store. This is especially important for larger deployments to prevent the Internet line from collapsing. Unfortunately, there is no specific timeline known here.
SCCM-Integration in Autopilot
Another change in Autopilot related to SCCM is that in future SCCM task sequences can also be executed on the client via Autopilot / Intune. This allows for some very interesting possibilities.
Updates for Autopilot
What actually works is that the autopilot can now download updates for autopilot when you run it and can thus be extended by functions on-the-fly. This is especially helpful when the OEM only provides images of the respective RTM versions. Prerequisite is 1909 or 1903 with the September update.
VPN support
With this feature, all I can say is, “FINALLY!!!!!”.
Announced is the VPN support for autopilot for Q1 2020 and requires an autopilot with the update function. The update function can be used to update the autopilot afterwards with this feature. This eliminates the need for the hybrid domain joins to have a direct connection to a domain controller. This means that users can finally perform the Hybrid-AD Join at home. In combination with White-Glove, the autopilot can finally be used even with narrow bandwidths. The important requirement is that the VPN client is packaged and distributed as Intune Software. The VPN client must also be able to connect to the tunnel before the user logs in.
Have I said already? Finally!!!!
Modern Authentication in Autopilot
Soon Autopilot will also support the log in via Authenticator App on the mobile phone or via FIDO2 Token.
Names are not so important, are they?
In the future, the naming scheme for autopilot and hybrid domain join will be aligned. It will also be possible for IT to specify selected names directly for a device.
Overview slides by Michael Niehaus on the innovations

New in Intune
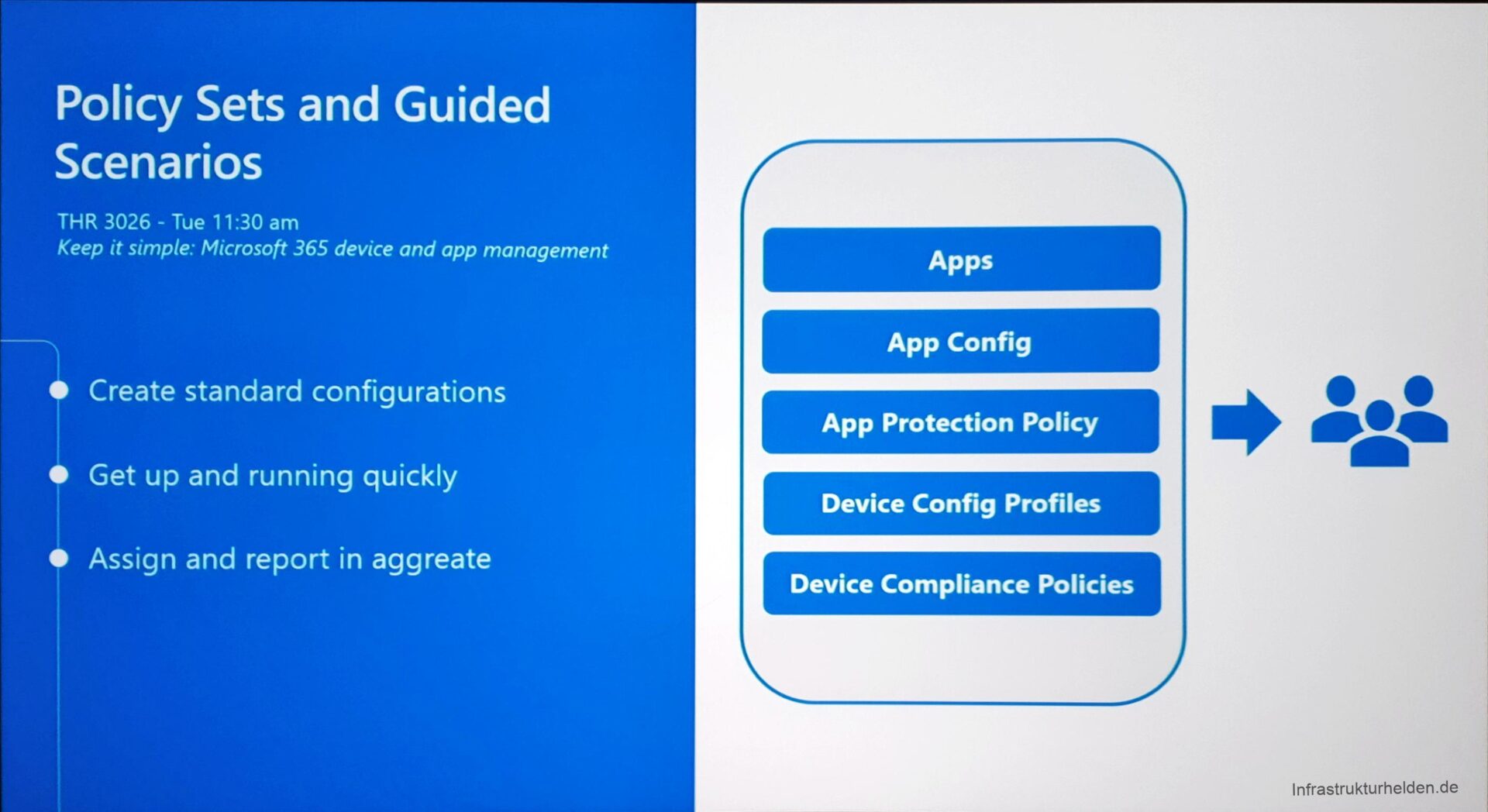
One of the new features in Intune is Policy Sets. These bundled applications, application configurations, and application protection policies together. This is intended to simplify administration for administrators. So only one Policy Set has to be assigned, instead of everything individually.
Also new is the so-called “Guides Scenarios”. These are a guided wizard through individual steps for certain scenarios and end in a finished policy set. The target group for this are new administrators or generalists who are looking for a simple start.
Note on transparency
At the time of writing, I was working for Dell Technologies. However, this article reflects my own personal opinion, and was not sponsored, influenced or rewarded by my employer in any way. Only the trip to Ignite was paid by Dell. #Iwork4Dell
This article first appeared on Infrastrukturhelden.de in German.
This article is a translation of the Infrastrukturhelden.de article “Ignite – Modern Management” (Published- 2019-11-06). Links may refer to other Infrastrukturhelden.de articles, these may also be available in English language.
Also it can be, that I still use screenshots of German systems. However, where it is possible for me with little effort, I insert screenshots of English systems.


Good replies in return of this difficulty with genuine arguments and telling all regarding
that.
Never waste your time by going there