Welcome to part 2 of the Azure-AD series. This part covers license types and features. We will also deal with the topic of license procurement and licensing possibilities. Due to the scope of functions, I cannot describe all functions contained in the individual licenses in this article. But I try to cover as much as possible and to provide links to further information.
Articles on the Azure AD series
The information in this article is as of May 2019, current prices and features can also be found at Microsoft under https://azure.microsoft.com/en-us/pricing/details/active-directory/
license types
There are 5 variants of the Azure-AD license, often one of these variants is already included in packages like Office365 E3 or Microsoft 365 E3. 3 of the 5 variants can also be licensed individually for a fee. Like most cloud licenses at Microsoft, this is based on the number of users. Whereby also a combination can be used.
Microsoft Azure-AD Free
Of course, the free version has the most restrictions. This variant is the only one that has a hard object limit, which is 500000 objects. But how big this number actually is, already shows that no matter which edition you use, a support call must be opened for more than 50000 objects. Objects in this case technically mean everything that has a “Distinguished Name”, mean everything, users, computers, groups, etc..
Further limitations are of course the missing basic and premium features. The basic features also include an SLA, which is not granted for the free version.
Microsoft Azure-AD Basic / Office 365-Apps
Since the range of functions is almost identical, I summarize these two license variants. In addition to an SLA, these two editions have other functions that distinguish them from the free license. These functions are for example:
Group-based access management and provisioning
This allows you to use groups to manage access rights. These can be mailboxes in Office365, for example, but also resources in Azure itself, such as access rights to Azure Log Analytics. This is also the basis for providing services and resources based on group membership.
Password Self-Service for Cloud Users
Cloud-based identities (No synchronized ones!) can reset their own passwords if they have been set up.
corporate branding
The company branding allows you to customize the login pages and ensures that Azure-AD based shortcuts will also display the individual company logo. This is, for example, a requirement of Microsoft Autopilot, but is already apparent in the normal login to Office365. Of course only after entering the email address.
application proxy
This is a reverse proxy that can be used to provide internal web applications over the Internet. For instructions on how to set this up, see docs.Microsoft.com.
Multi-factor authentication (Office 365 Apps only)
Multi-factor authentication is also available for accounts with administrative rights in Office 365 / AzureAD. For more information, see Azure-AD P1: Multi-Factor Authentication.
Azure-AD Premium P1
Azure-AD Premium P1 includes all features of Azure-AD Free and Basic, plus a few premium features:
Advanced group functions
By extended group functions, Microsoft understands dynamic groups, authorization management for group administration, group flow and still some further functions approximately around groups.
Password self-service to reset
Allows users with enabled write back also for on-premise users who want to change and unlock their own password.
Two way synchronization for devices
This allows the transfer of Azure-AD devices to the local Active Directory. However, these are not normal computer accounts, as is the case with a hybrid join. However, this function is required for “Conditional Access” with ADFS protected access. Azure-AD devices can be used as an authentication factor just like AD devices.
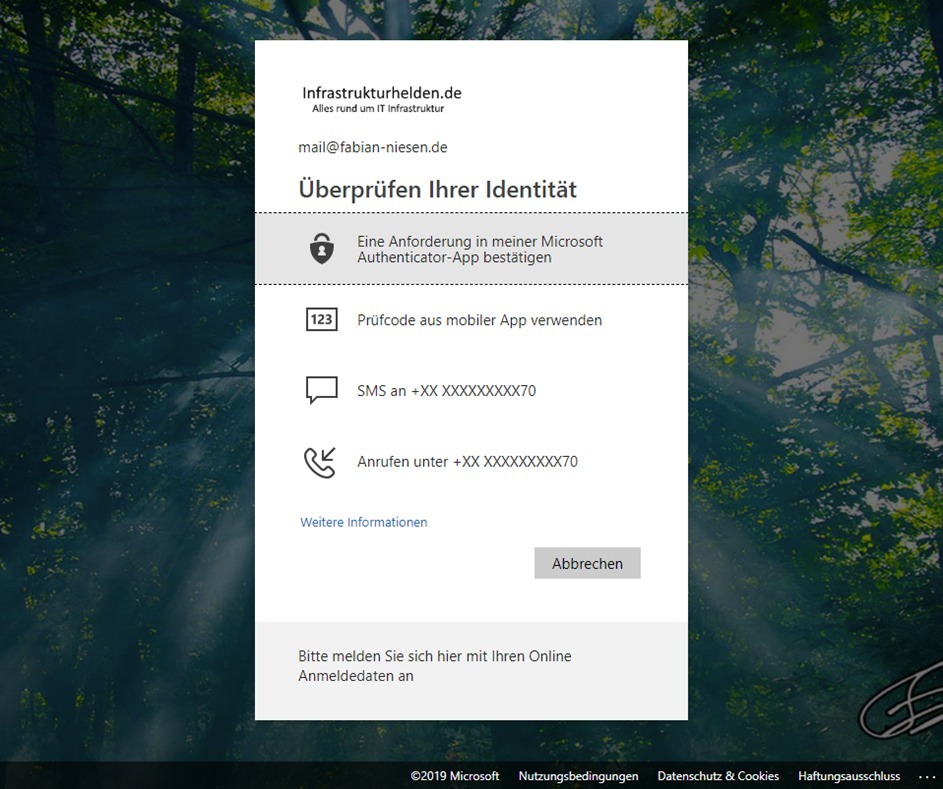
Multi-factor authentication
With multi-factor authentication, authentication can be secured with other factors. As with a classical MFA, a distinction is made between the factors:
- Knowledge: For example the password
- Ownership: For example, a trusted device such as a personal smartphone or a security token
- Biometrics: for example fingerprints, facial patterns, retina or vein scans
The Azure MFA Service can operate either in the cloud or as a local server with ADFS in its own environment. The second option is particularly interesting for companies that want to keep everything related to authentication in their own environment.
The advantage of Azure-MFA is that you do not need a token with additional costs. The following factors are available as possibilities for the factors without a lot of configuration:
- Microsoft Authenticator APP for push notification and one-time password generator. The Microsoft Authenticator app is available free of charge for Android and iOS.
- Code delivery via SMS (phone number must be stored)
- Code delivery via voice call (telephone number must be stored)
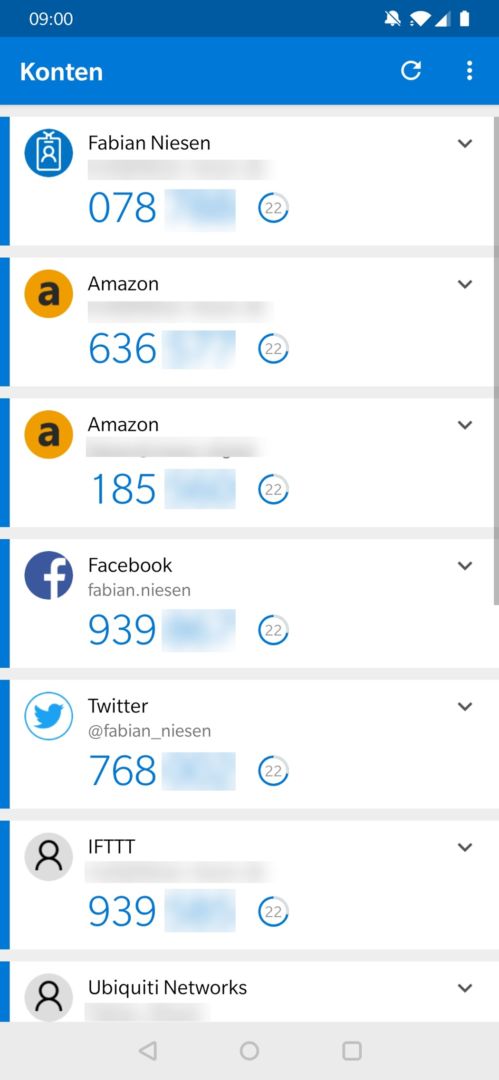
Another advantage of the free Microsoft Authenticator APP is that it can also generate a one-time password for other accounts, for example:
- Amazon
- IFTTT
- Microsoft Live ID (Live.com / Outlook.com)
- And many others that support the corresponding standard
Microsoft Identity Manager User CAL
If the free AD-Sync is not enough for you, you might think about the Microsoft IDM solution. Starting with Azure AD P1 is the user CAL, which is needed for it is already included. Therefore, this aspect of licensing no longer needs to be considered for users with the corresponding Azure AD license.
Cloud App Discovery / Microsoft Cloud App Security Integration
This product can be used to analyze the use of cloud services. The data traffic is analyzed and more than 16000 different applications from a catalogue maintained by Microsoft are covered. This is done by analyzing firewall and proxy logs, among other things.
The objective is to track down the so-called shadow IT. These are the systems that are not managed by IT but are used for business purposes. More about this product at https://docs.microsoft.com/en-us/cloud-app-security/set-up-cloud-discovery
There is also a Youtube video on this topic, for example how it works with Windows Defender ATP (WDATP). The video is in English and a recording of the Microsoft Ignite Conference 2018. https://www.youtube.com/watch?v=f8hbvbY1Hnc
Connect Health
With Connect Health, you can monitor the connections between the systems involved in authentication. This applies not only to Azure-AD Connect but also to ADFS when it is in use. Alerting can be done by email, for example. You can find out more about this product at https://docs.microsoft.com/en-us/azure/active-directory/hybrid/whatis-azure-ad-connect
Conditional Access
This function can be used to control access to resources more precisely. For example, access to certain systems can only be granted from company devices that comply with company rules. Another example would be location-based, if, for example, certain systems may not be used from certain countries. Even if the user would normally have access, he is prevented from doing so on a business trip or vacation in that country.
Azure-AD Premium P2
Identity Protection
With Identity Protection, user accounts can be secured. Among other things, user behaviour and machine learning methods are used to analyze risks. Depending on the risk identified, automatic measures can be taken, such as requesting further authentication factors when logging on or refusing to log on.
For more information, see https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/overview
Privileged Identity Management (PIM)
Privileged Identity Management allows role-based management of privileged rights. It also enables functions such as just-in-time, time-limited or approval-obligated assignment. It is also possible that the user has to document the reason for the extended rights or that a notification is sent. Of course, history can also be generated for audit purposes.
Further information on PIM can be found at https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-configure
Access Reviews
With Access Review, Microsoft provides a function that is dedicated to the topic of access rights and their lifecycle. Examples that Microsoft names for this solution are among other things:
- Analysis of Privileged Rights
- Checking authorizations after changing the employee’s role (for example, in the case of a change of department)
- Regular review – Are the rights still needed?
- Do new employees have the necessary permissions?
You can find out more about this topic at https://docs.microsoft.com/en-us/azure/active-directory/governance/access-reviews-overview
Notes on license topics
I’m not a licensing expert! Also, the changes are so fast moving that it would hardly be possible to update the articles. Therefore, always ask your licensing consultant about licensing topics. All information in this article is without guarantee.


Good post! Thanks!