In this article we will show you how to install and set up a VPN server with Windows Server 2022. We will go through the setup step by step.
This article is based on the article VPN Server with Windows Server 2019 (RAS) and has been updated for Windows Server 2022.
To access the corporate network and access corporate resources while on the road, there is rarely any way around a VPN. A virtual private network is one of the dial-up and connection options of a remote access server (RAS). Since modem and ISDN dial-up connections are rather extinct today, these systems are almost only used for VPN dial-ups. Nowadays, integrated solutions from firewall providers such as Juniper, Cisco, Unfiy and others are often used for this purpose.
As a basis for my installation I take a VM with 2 vCPU and 4 GB Ram, for the few VPN connections that are needed here this is perfectly sufficient.
Here’s another warning for safety
This is for my test environment, accordingly the security requirements are not as high as for an enterprise RAS server. For companies, I recommend a hardened reverse proxy in a DMZ, for example a Kemp Loadmaster, which still provides some security. Also, multi-factor authentication should be considered.
You should also think about the structure in advance. RAS implementations range from very simple to highly complex. It is important to find the right one for you.
Operating system installation
After installing Windows Server 2022, the system should first be provided with the latest updates. Start with the installation of the server role “Remote Access”, which includes not only the RAS services with VPN protocols such as PPTP, DirectAccess, SSTP and L2TP/Ipsec, but also a reverse proxy for web applications or a routing service. You should not install the latter as well.
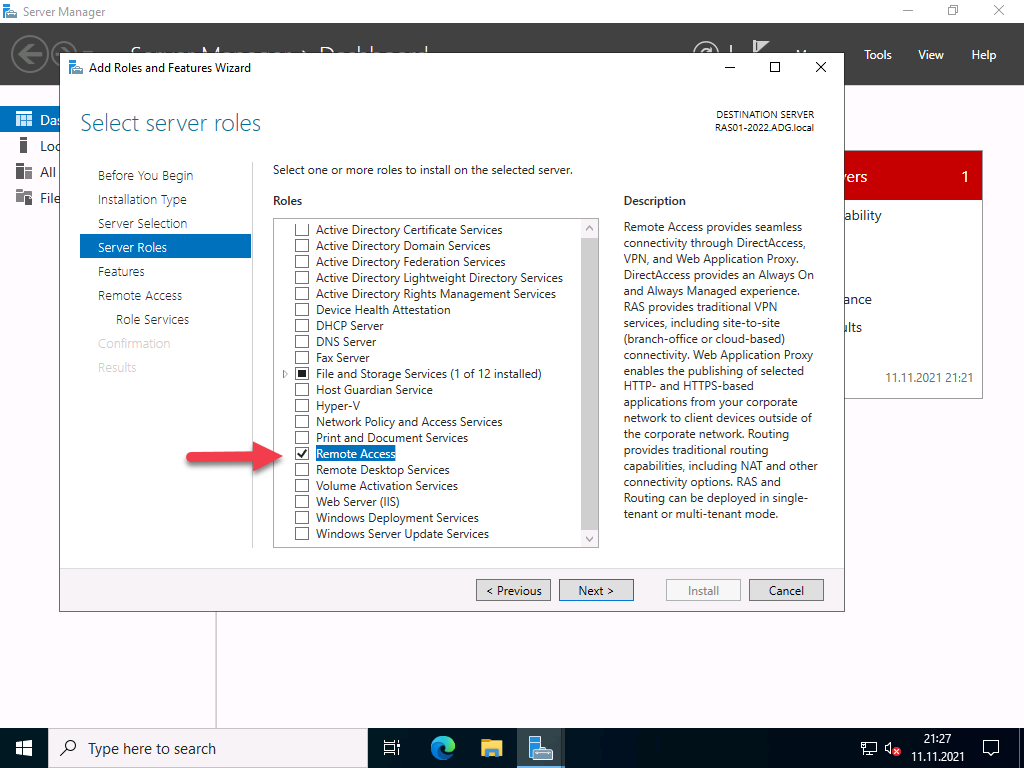
You must select which of the 3 function types you want to use in the role services. Select “DirectAccess and VPN (RAS)” here.
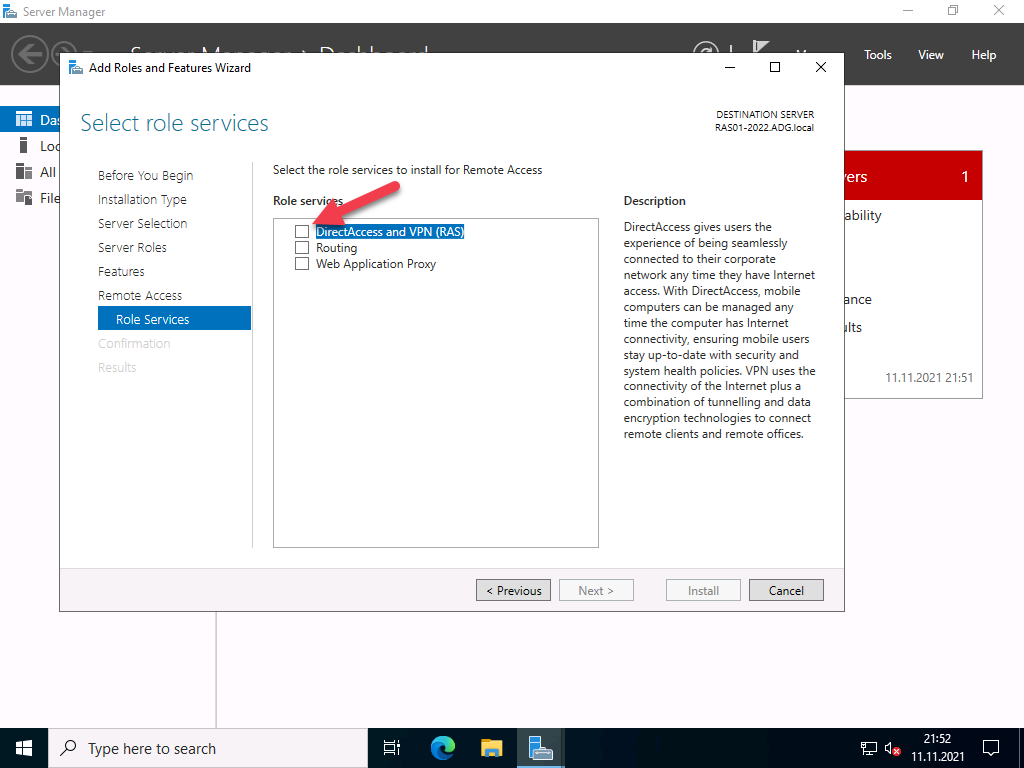
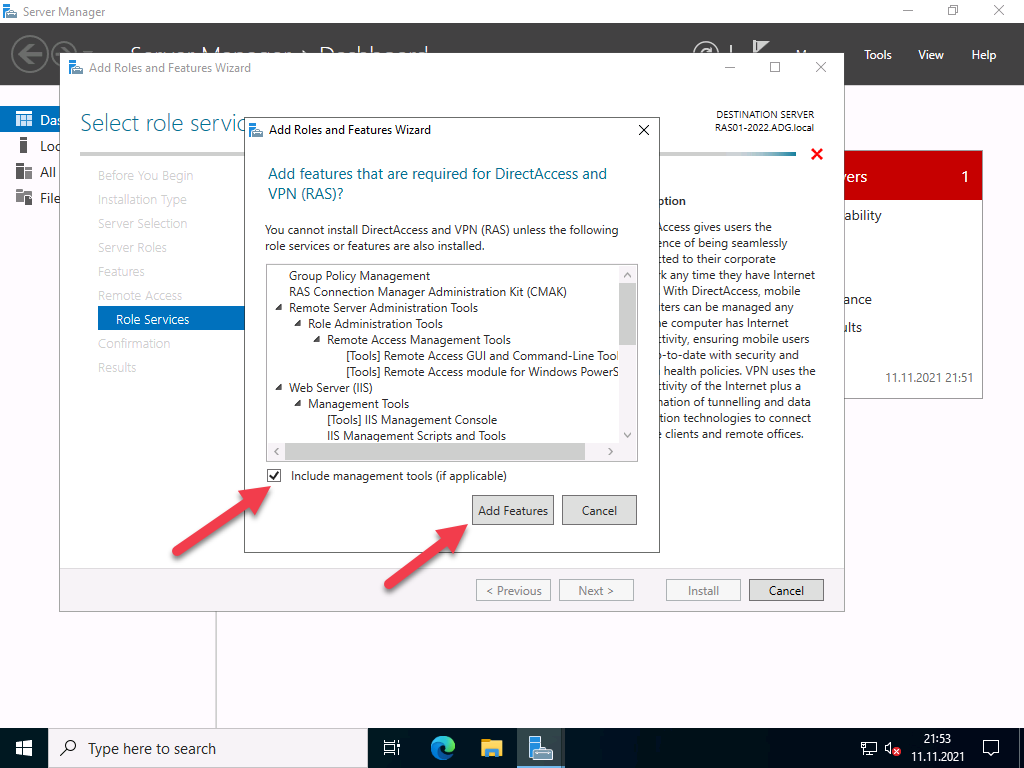
After the selection, the required dependencies are displayed. Please confirm them.
No further configuration is required for easy installation.
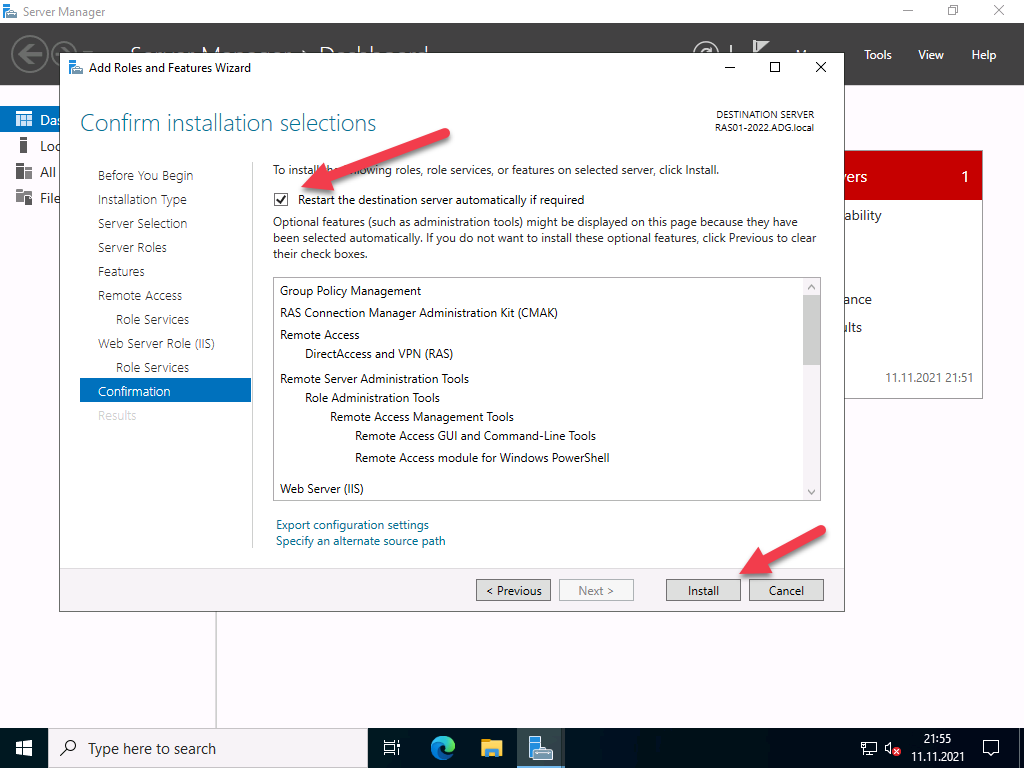
Start the installation and restart the server if necessary. A restart should not actually be necessary.
After installing the roles, the “First Steps Wizard” must be executed.
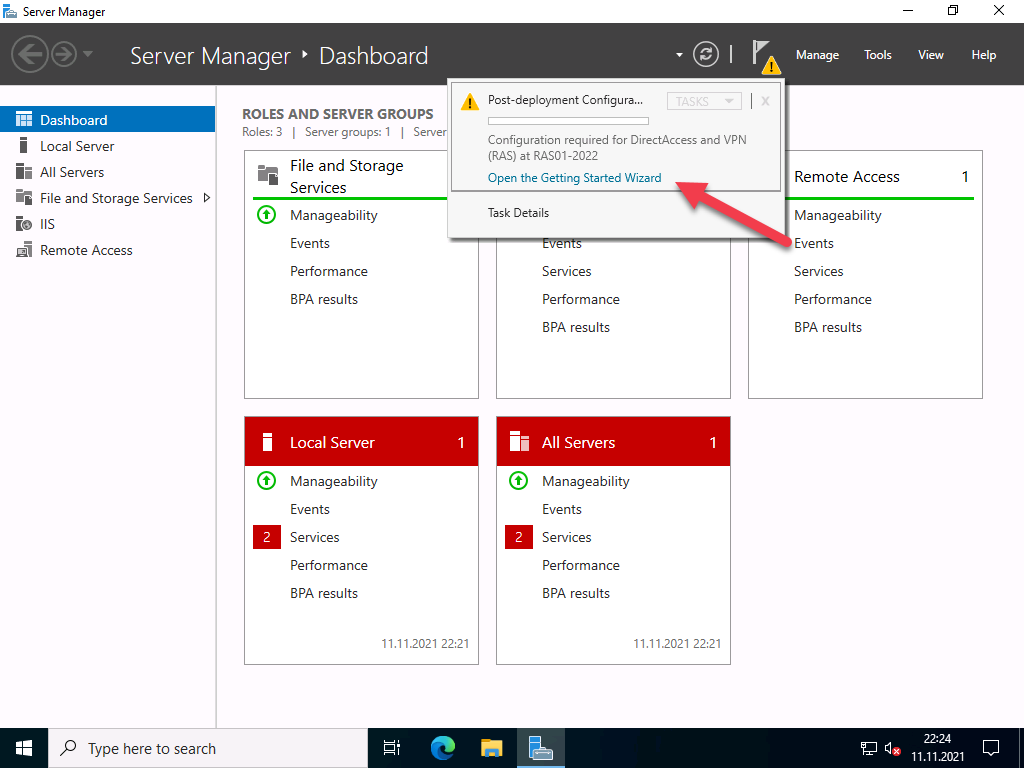
For most scenarios, a VPN connection is perfectly adequate. In addition, DirectAccess also brings IPv6 dependencies with it. So for now, we will only deal with VPN.
The “Routing and RAS” console opens, which has not changed since Windows Server 2008.
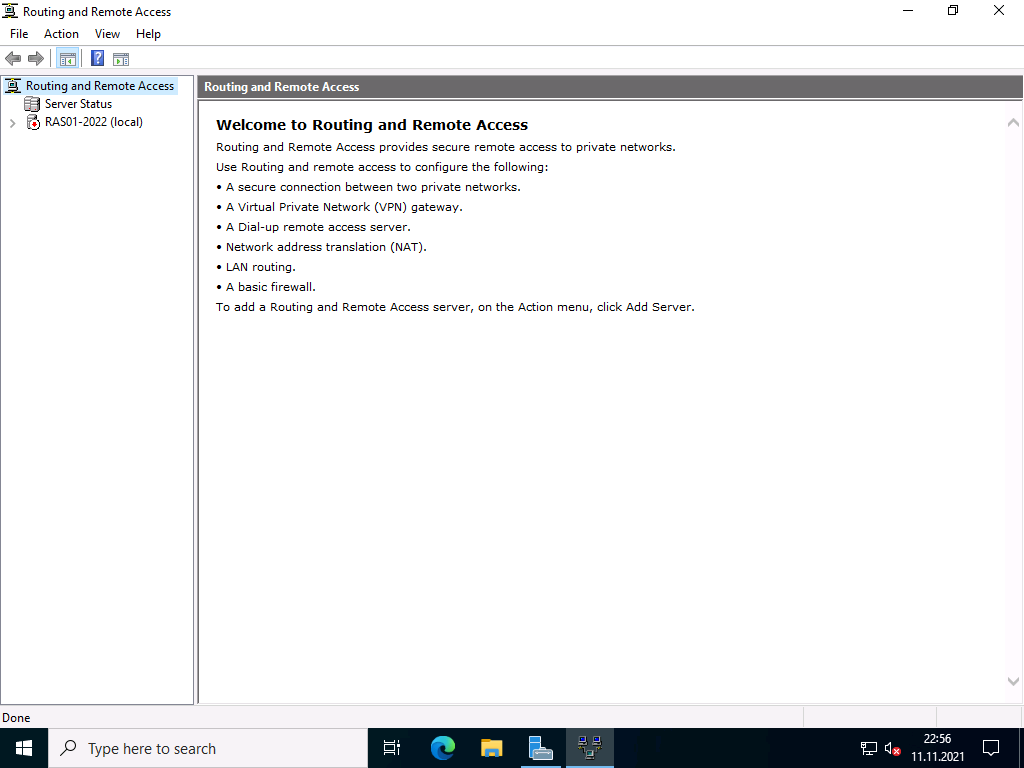
Right-click on the server and select “Configure and activate routing and RAS”.
Click on “Next” in the setup wizard
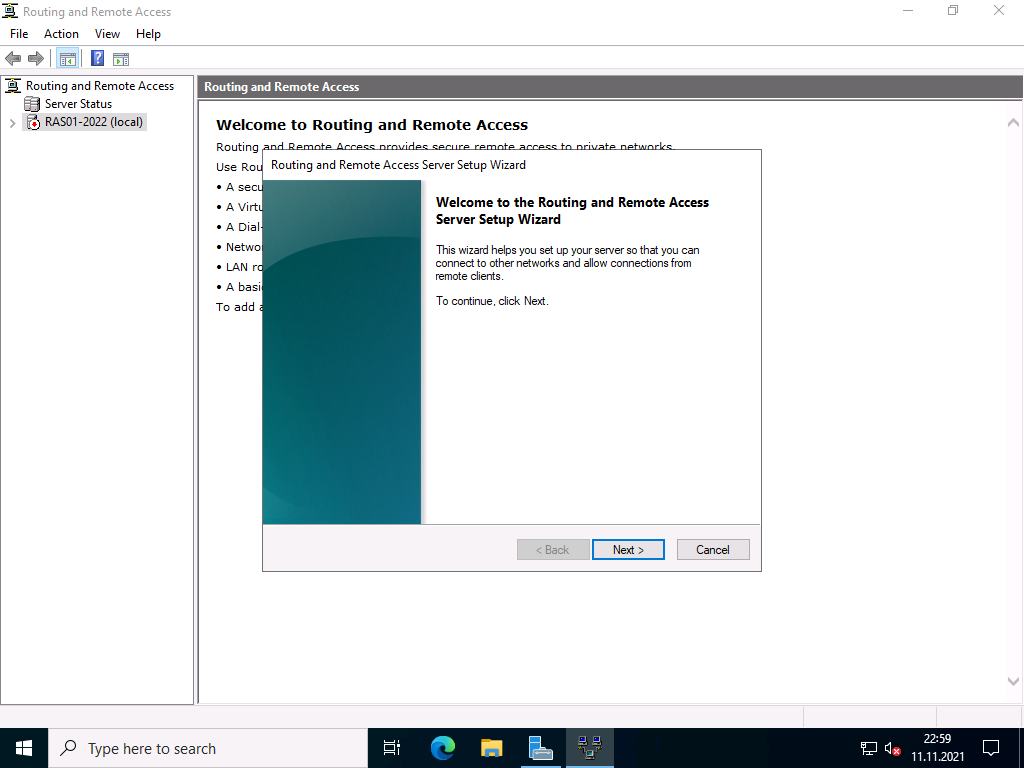
In the next step you have to specify more precisely which scenario you want to set up. Next, I choose the “Custom Configuration” because “RAS (Dial-up or VPN)” expects certain requirements that we do not need.
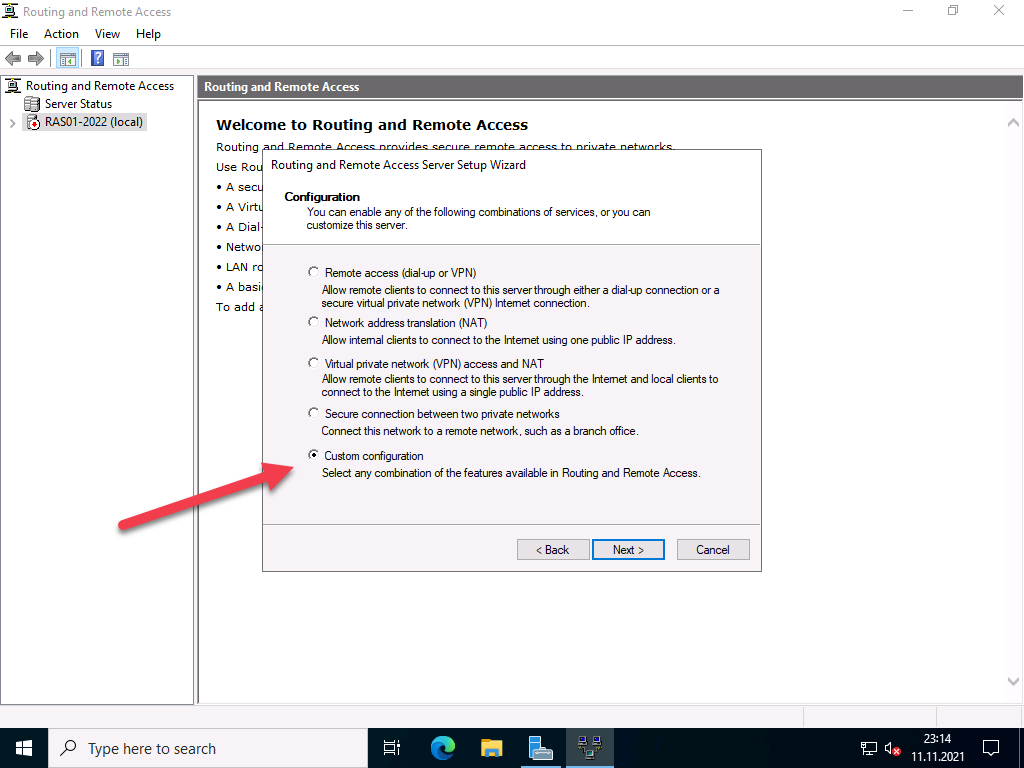
In the next step, select “VPN access”
In the next step, you complete the configuration selection.
Confirm the message to start the service.
Afterwards, the VPN protocols can be configured.
Configuration of the VPN protocols
Supported protocols
- PPTP (Point-to-Point Tunneling Protocol) the first implementation was in Windows NT 4.0. Communication takes place via port 1723 TCP and the protocol 47 GRE. PPTP is widely used, but is no longer secure enough today, see also Microsoft security recommendation 2743314.
- L2TP (Layer 2 Tunneling Protocol) which is used by Microsoft together with IPsec. Communication takes place via port 1701 TCP and 500 UDP.
- IKEv2 (actually “Internet Key Exchange V 2”, but here a synonym for IPsec, IP Security). Communication takes place via port 500 and 4500 UDP.
- SSTP (Secure Socket Tunneling Protocol), a Microsoft own protocol based on port 443 TCP. Thus, it gets through all firewalls as long as the HTTPS tunnel is not broken. The protocol requires a functional SSL tunnel. Disadvantage: only available on Microsoft devices.
Protocol selection
The choice of protocols depends on several factors. Each protocol has strengths and weaknesses.
For me personally, the best thing about SSTP is that it works everywhere. Even in free hotel WLANs, which actually only allow VPN in paid WiFi. The disadvantage is that I need a valid certificate from a trusted CA with a public revocation list. This rules out most internal certification authorities, because they do not have public spear lists. Alternatively, a regkey can be set in the client so that this is ignored. SSTP is also only supported by Microsoft operating systems.
PPTP is too insecure for most people, but is supported by almost all end devices.
L2TP is compatible with most devices, depending on the configuration. But in this configuration is the tricky part.
The same applies to IKEv2 / IPsec, depending on the type of authentication, there is quite a bit of work to be done here.
Basic configuration of the protocol ports
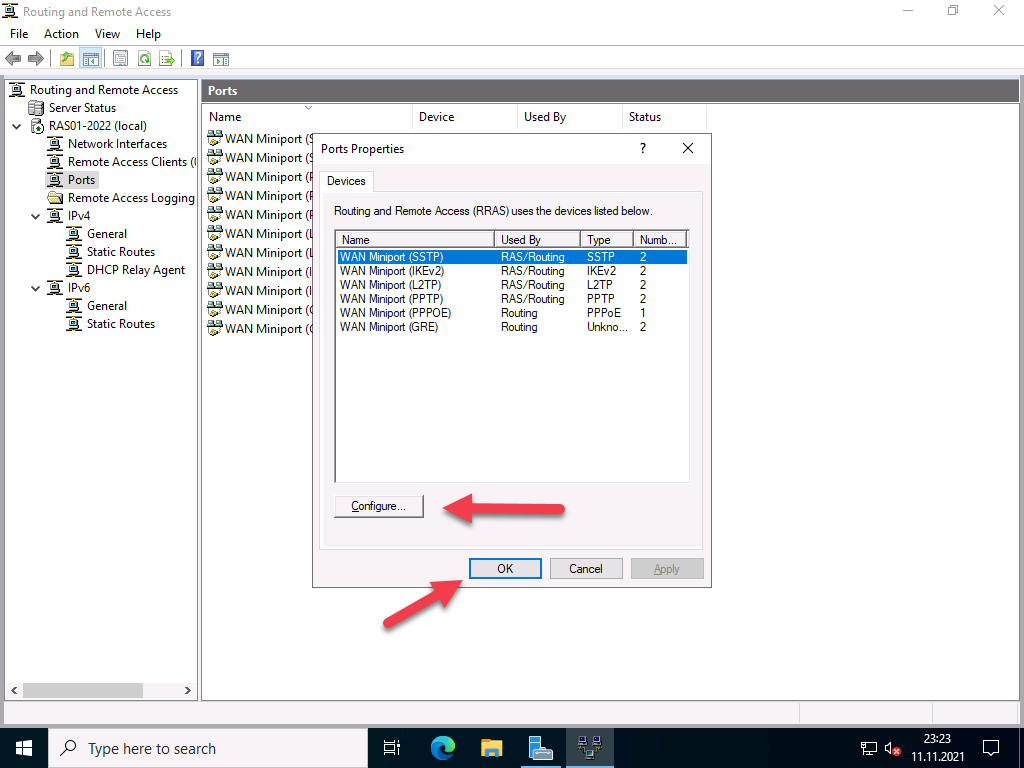
The wizard initially created 2 ports for each protocol, except for PPPoE, which only has one. Depending on the selection of protocols and the expected connections, I would disable unused ports or add new ones. With Windows Server 2022, the number of standard ports has been significantly reduced; with previous versions, up to 128 ports were created.
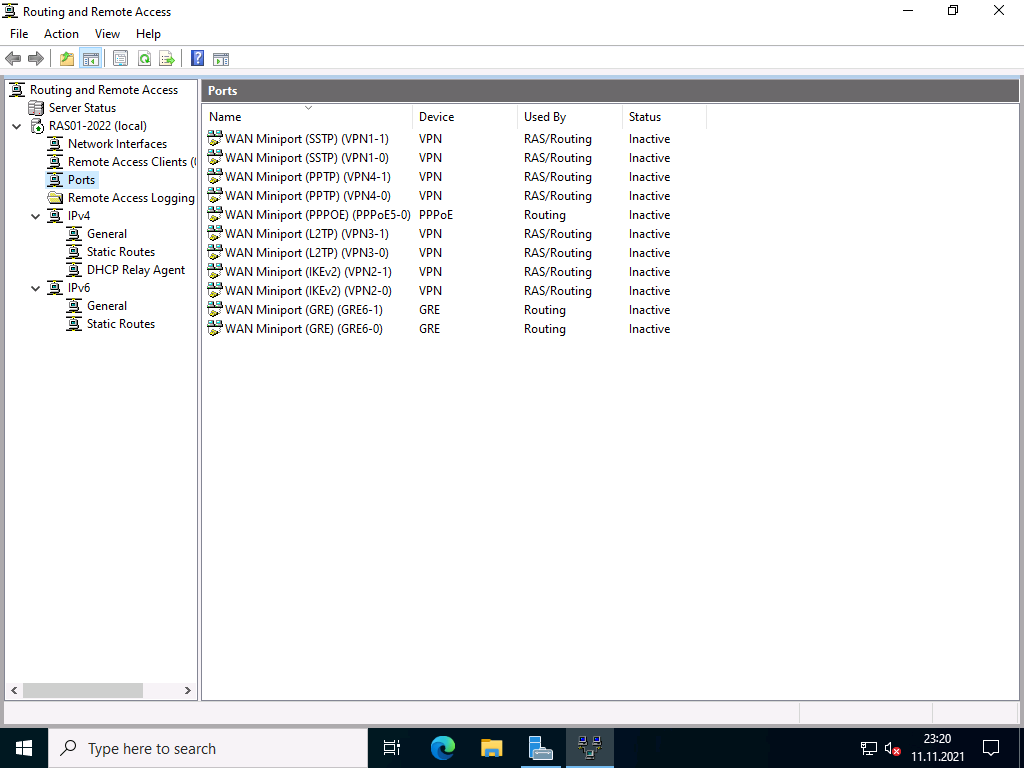
To do this, right-click on “Ports” and select “Properties”.
In my case, I switch off the protocols I don’t need and reduce the ports to 1. For the protocols I do need, I leave the number of ports at 2, which is enough for me.
Configuration of the IP address ranges
The clients that connect remotely need a private IP address. The DHCP server in the network can be used for this, or a static range can be assigned. This is managed by the RAS server.
Firewall configuration
Since the RAS server is not located in the DMZ and does not have a public IP address, port forwarding must be set up on the firewall for the ports of the selected protocols. It is important that the RAS server has a static IP address or a DHCP reservation.
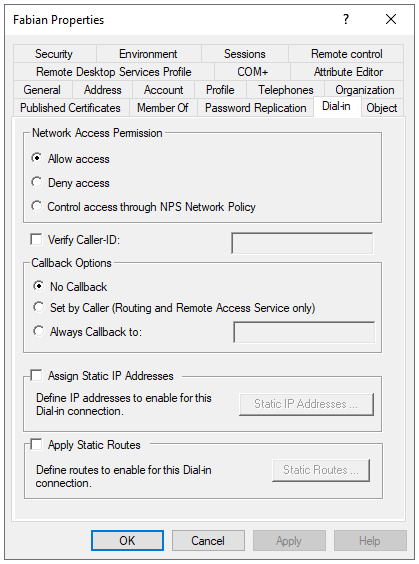
Assigning rights for users
It is also important that the users have the necessary rights for remote access.
Read also our article: SSTP VPN with Let’s Encrypt certificates.
